Deploying an Application with an IaaS infrastructure on a Protect Landing Zone
Use cases
- You are interested in exposing an application for Thales RIE only with security guarantees
- You have opted for PaaS services to minimize your operating expenses
- You don't want to use Kubernetes
- Your application does handle C3 data
Architecture schema
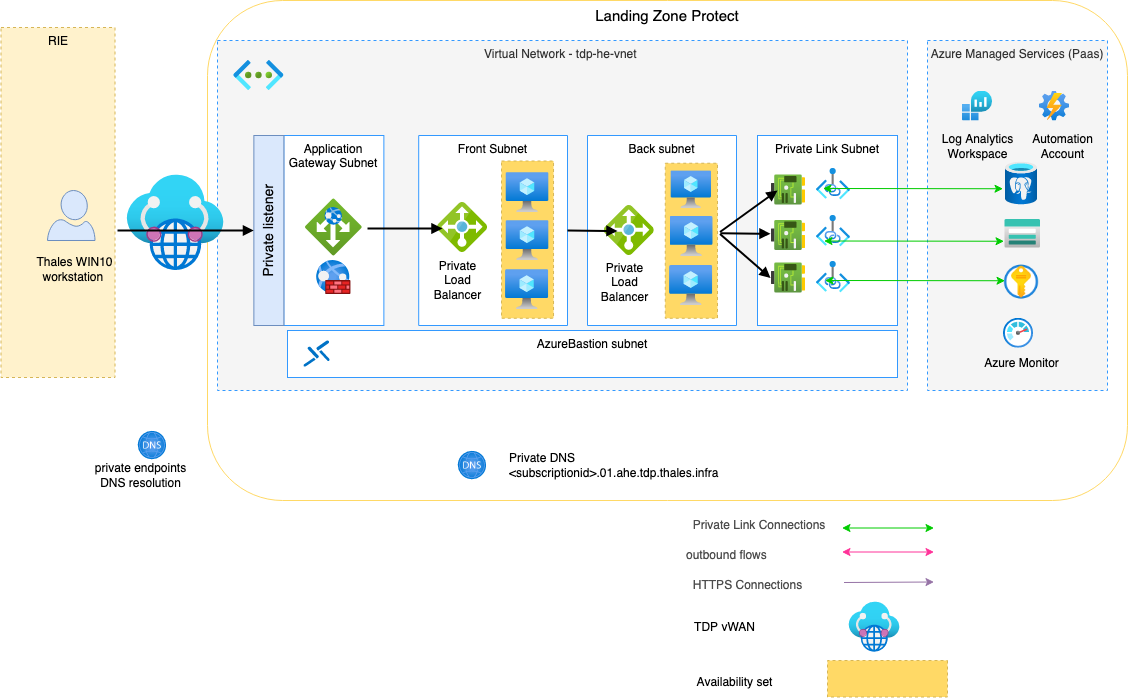
Design description
On top of a Protect Landing Zone, an VM Scaleset infrastructure to host an application accessible from the Internet.
The application will not be directly exposed to the Internet at all but accessible from Thales RIE.
The application will consume various Azure managed PaaS services such as:
- a PostgreSQL database
- a Keyvault for storing application certificate and database credentials
- a storage account for your application static files
Every service will be accessed through a private link rather than over the public network.
7-level security will be ensured by enabling Web Application Firewall on the Application gateway.
Constraints
Exposure
Reachable privately by the application only:
- PostgreSQL database
- Keyvault
- Storage account
Reachable from Thales RIE networks only through a private gateway:
- Application
Monitoring and Patch Management
When deploying Virtual Machines, a set of policies in the Innovate Landing Zone will deploy monitoring agents automatically configured to send logs to the Log Analytics Workspace of the Landing Zone, and onboard the Virtual Machines with the Automation Account to provide Patch Managemnt Capabilities.
Refer to our documentation for more infos :
Application Gateway
- With a Standard Public IP and a private frontend endpoint
- When deploying the Azure Application Gateway (Deploy Azure Application Gateway), choose either WAF_V2 or Standard_V2.
- From the Backend settings, select "https" as the Backend protocol. In "Trusted root certificate" section, the backends must be in the allowlist of the application gateway. Upload the public certificate of the backend servers to this Backend setting.
Load Balancers
- With a Standard Public IP and private exposure
DNS resolution
Each Protect Landing Zone is delivered with a private DNS zone (<subscriptionid>.01.ahe.tdp.infra.thales).
Custom DNS servers are deployed at the TDP level and when the landing zone is delivered to you, tdp-he-vnet network has already been configured with them.
Private DNS Zone
This DNS zone contains entries to be resolved within the virtual network tdp-he-vnet.
- You may want to create an additional private DNS zone with a shorter and friendly name. Refer to the page here to know more about it.
- Virtual Machines will register automatically in the private DNS Zone.
- Internal Load Balancers require their DNS records to be manually added to the DNS zone
Thales Internal DNS resolution (*.corp.thales)
- For your application to access to a Thales Internal service from your Landing Zone
- For the Thales users to access to your application from the Thales RIE
*.corp.thales DNS resolution will rely on our own DNS servers that will relay requests to Thales.
Private endpoints case
For all the private endpoints you will need to connect Azure PaaS Services to the tdp-he-vnet virtual network, you do not have to create additional DNS zones since it will rely on existing Azure DNS zones out of the IaaS Landing Zone.
At the Private endpoint creation time, set "Private DNS integration" to "No". Integration to our DNS infrastructure is already in-place. Refer to our documentation.
The private endpoint creation will automatically be detected and trigger the DNS registration of the needed A record in our fully-managed private DNS zones. Thanks to this, DNS resolution of the private endpoints will also be possible from other subscriptions.
Certificate management
If you need to configure server certificate renewal on the application gateway, please refer to our documentation
PostgreSQL Server
- You need to select either General Purpose or Memory Optimized sku
- Change "Deny public network access" to Yes.
- The PostgreSQL server will only be accessed from the VMs of the virtual network. To achieve this purpose, you'll have to create a Private endpoint connected to services dedicated subnet.
- Enforce TLS 1.2 version as the minimum TLS version.
Storage Account
- Secure transfert must be enabled
- Public access must be disallowed
NSGs
- No inbound traffic from Internet and it's not possible to expose on an Internet public address.
Networks
- Virtul network of THALES range exclusively will be provisioned along with the Landing Zone taking into account the range size you have specified through your Landing Zone creation request. Check our documentation the different range sizes that are available.
- No external peering except for the vWAN
Network interfaces
- No public IP should be configured
- No IP forwarding enabled
Troubleshooting
Consult Troubleshooting page