Configure Patch Management
Each Azure landing zone provided by the TDF include a preconfigured Azure Log Analytics solution named Update Management. Goal of this solution is to help TDF BL consumer in managing update status of their virtual machines and organize patch deployment. Required vocabulary is available in the Glossary.
Introduction
Every Azure Hardened subscription (C2 & C3) includes a resource group named tdp-he-monitoring-rg. that contains multiple resources such as:
- An Azure Automation account dedicated to the update management solution
- The Azure Log Analytics workspace dedicated to the Azure subscription
- Some Azure Log Analytics solutions
By default, every Virtual machine you will be deploying within your Azure Hardened subscription will be automatically onboarded to the Update Management solution. This solution is deployed into a dedicated instance of Azure Automation Account named tdp-he-automation-account as illustrated bellow:
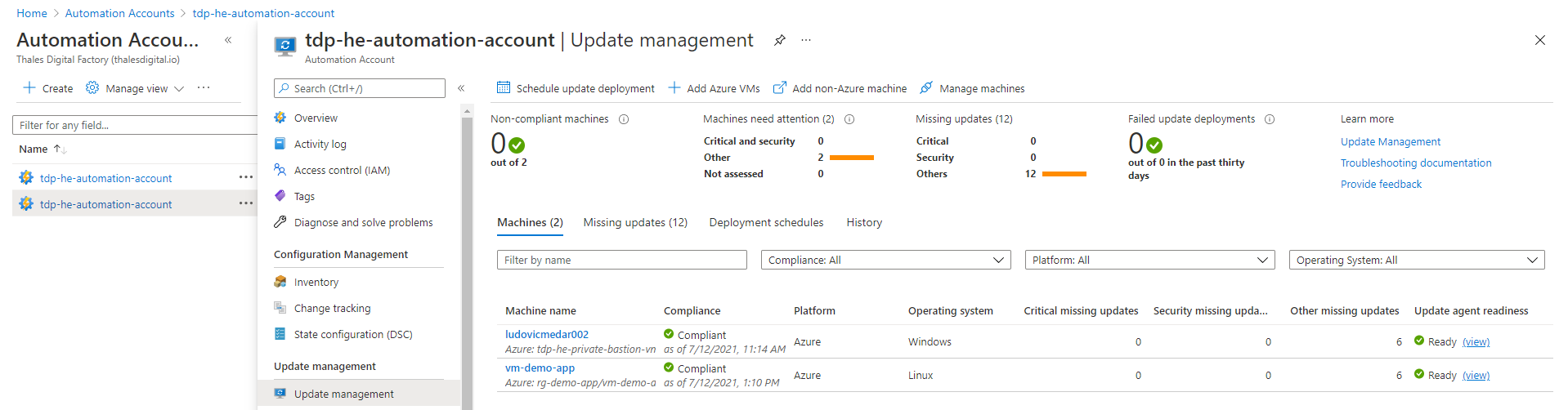
Solution will be providing the following information related to the patch status of your workloads:
- Virtual machine name
- Operating system
- Critical missing updates
- Security missing updates
- Other mission updates
- status of the agent (in the virtual machine)
Using the Update Management solution, you will be able to :
- Track patch situation of your virtual machines (up to date, missing updates, reboot required, ...)
- Track missing updates that need to be deployed (applicable to both Windows and Linux workloads)
- Organize deployment of updates using deployment schedules
- Create an update strategy with group membership filtering or advanced filtering criteria
- Track the deployment schedule status over the time
The list of supported Linux OS is available in the Official documentation
Related services
Log Analytics
Update Management solution rely on Log analytics workspace to collect and process data. Every virtual machine in your Azure subscription is automatically configured to onboard to your Log Analytics workspace available in the tdp-he-monitoring-rg resource group. You can perform queries on the following tables using Kusto Query Language :
- Update
- UpdateSummary
Azure Security Center
Every Virtual machine in your Azure hardened subscription will appear in Azure Security Center and report for compliance purpose using recommendations. Some recommendations are focusing on Virtual machines. In illustration bellow we have the "System Updates should be installed on your virtual machines" recommendation with the healthy status. This means that all virtual machines in your Azure hardened subscription comply with the recommendation.
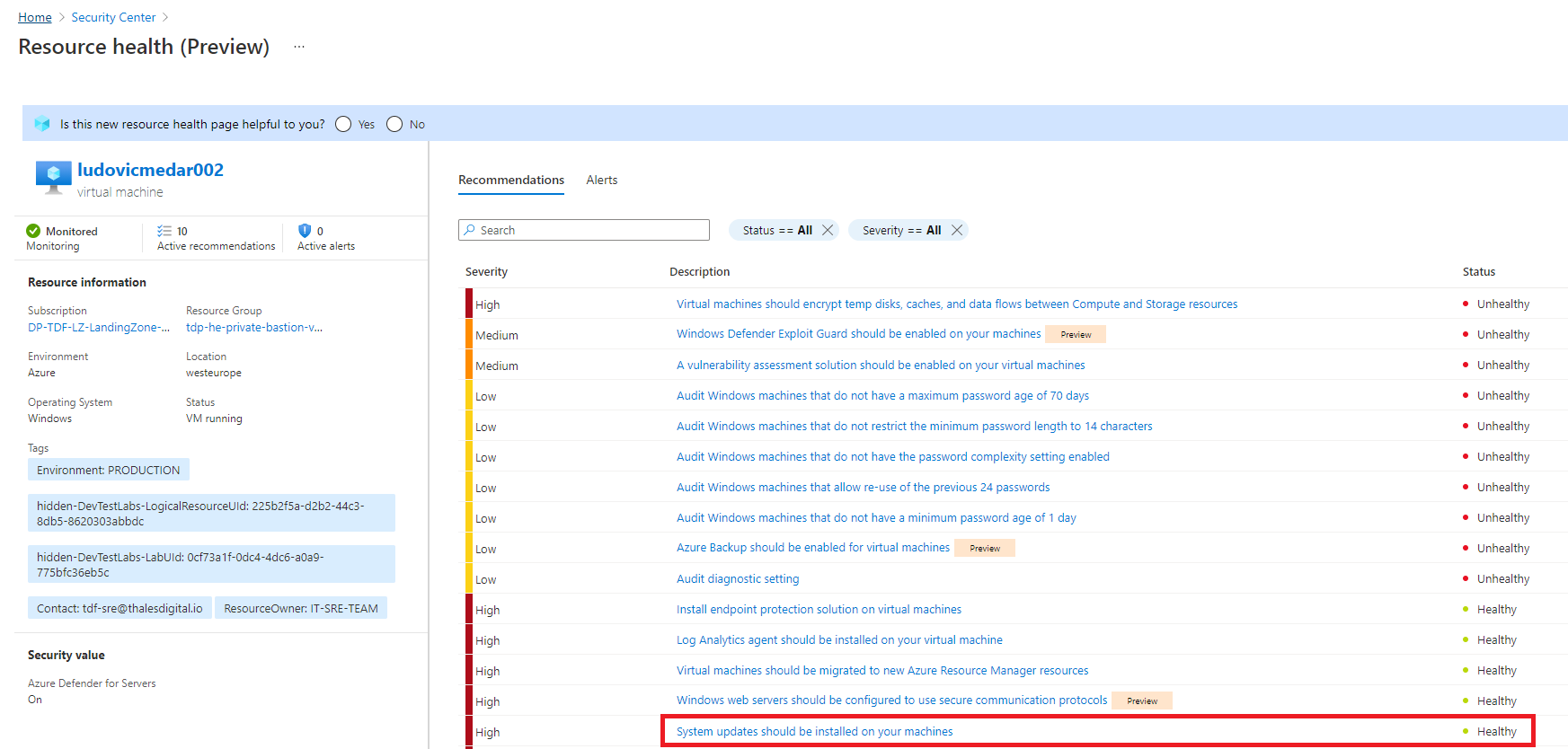
Because Azure Security Center is connected to the TDF SOC, Virtual machines that does not comply with security recommendations are detected by the SOC team.
How to
Track patch management status of your virtual machines
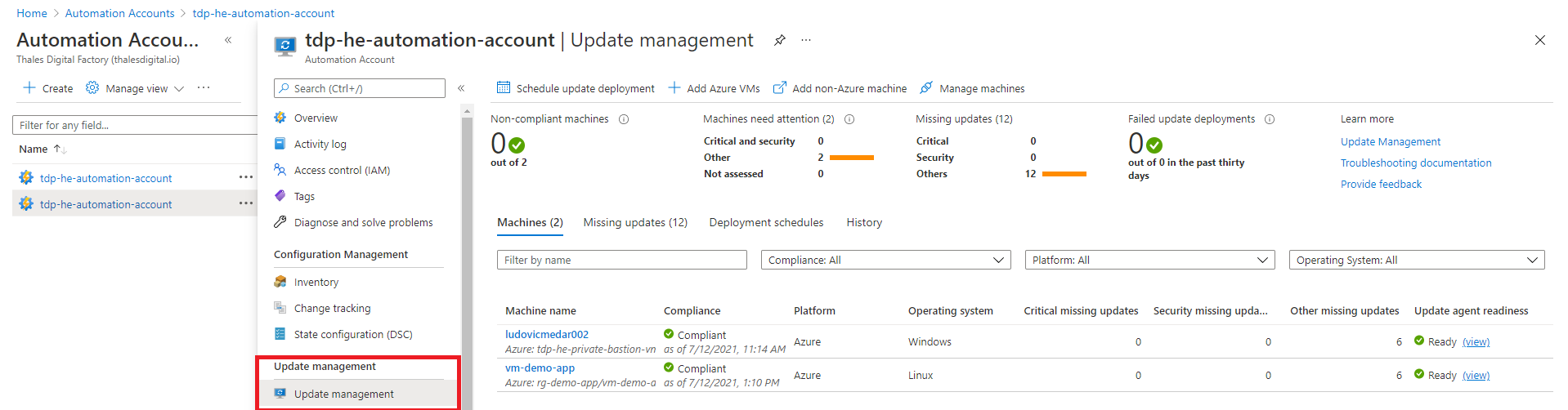
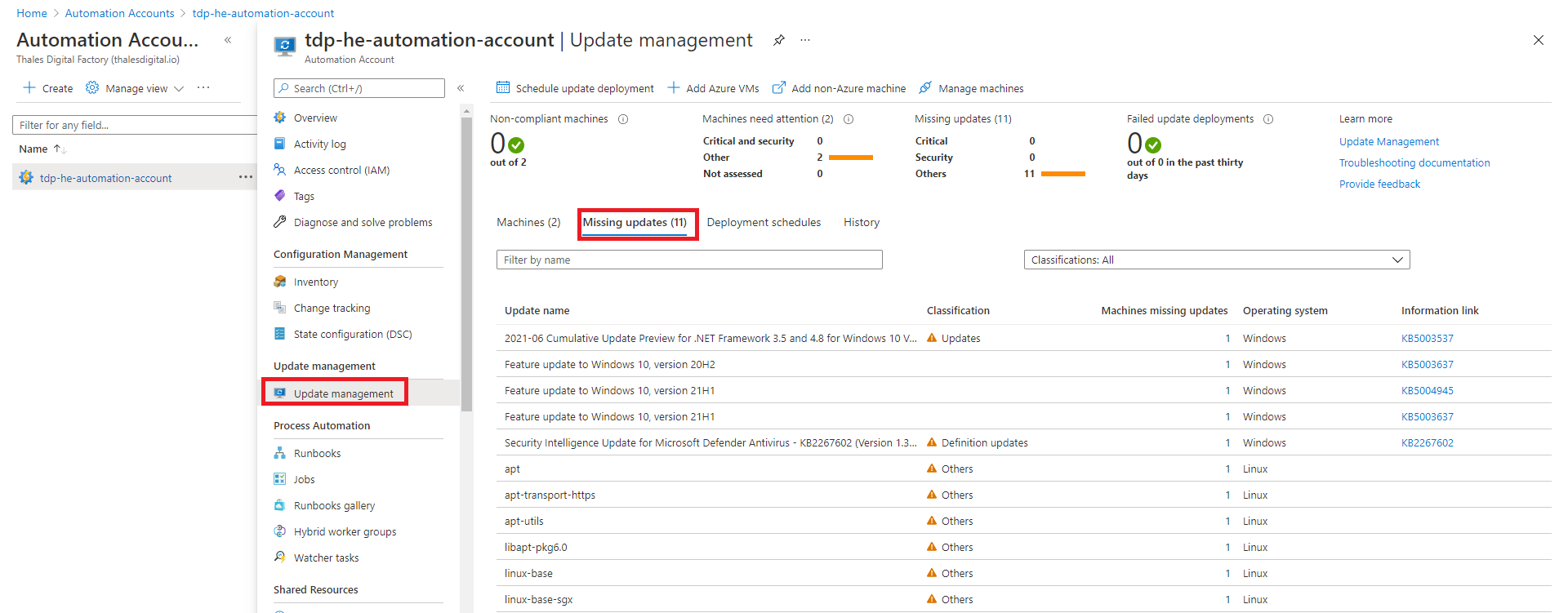
You can monitor the patch management status of your virtual machines using multiple ways. First, from the Azure Automation Account resource. In every Azure hardened subscription, this resource is in the tdp-he-monitoring-rg resource group and named tdp-he-automation-account. Just click on "Update Management" node as illustrated bellow :
Because the Update Management solution rely on Azure Log Analytics workspaces. Every Azure subscription have a dedicated Log analytics workspace resource located in the tdp-he-monitoring-rg resource group. As illustrated bellow, you can use the Kusto Query Language to perform queries. Virtual machines send their update management status based on a cycle (not the same for Windows and Linux).
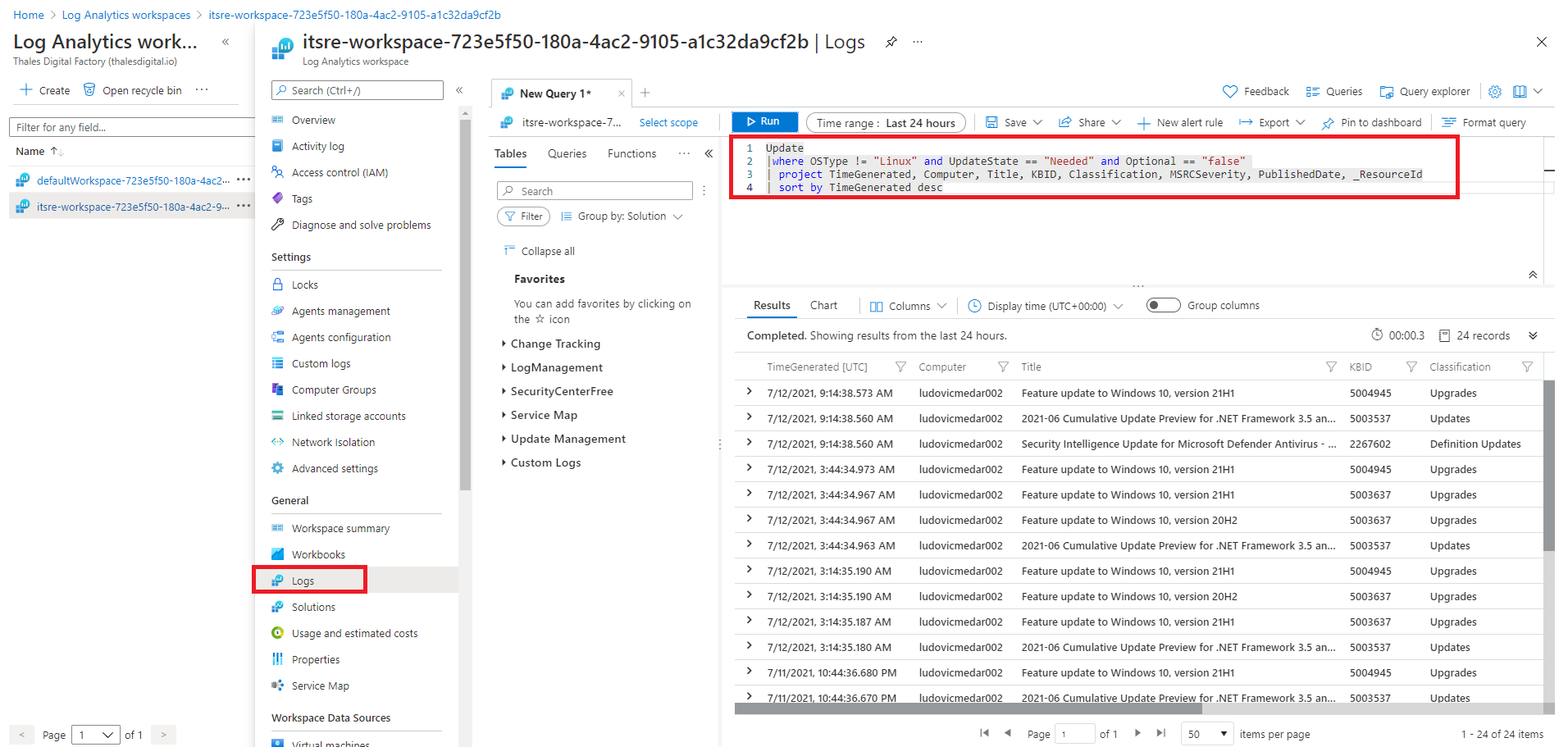
You can find more advanced queries here: Query Update Management logs. You can use these queries to create Azure alerts and initiate responses using action group.
At last, Azure Log analytics workspace provide a preconfigured dashboard. From your dedicated Log analytics workspace (available in the tdp-he-monitoring-rg), just click on Worskpace summary and select the "System UpdateAssessment" as illustrated bellow:
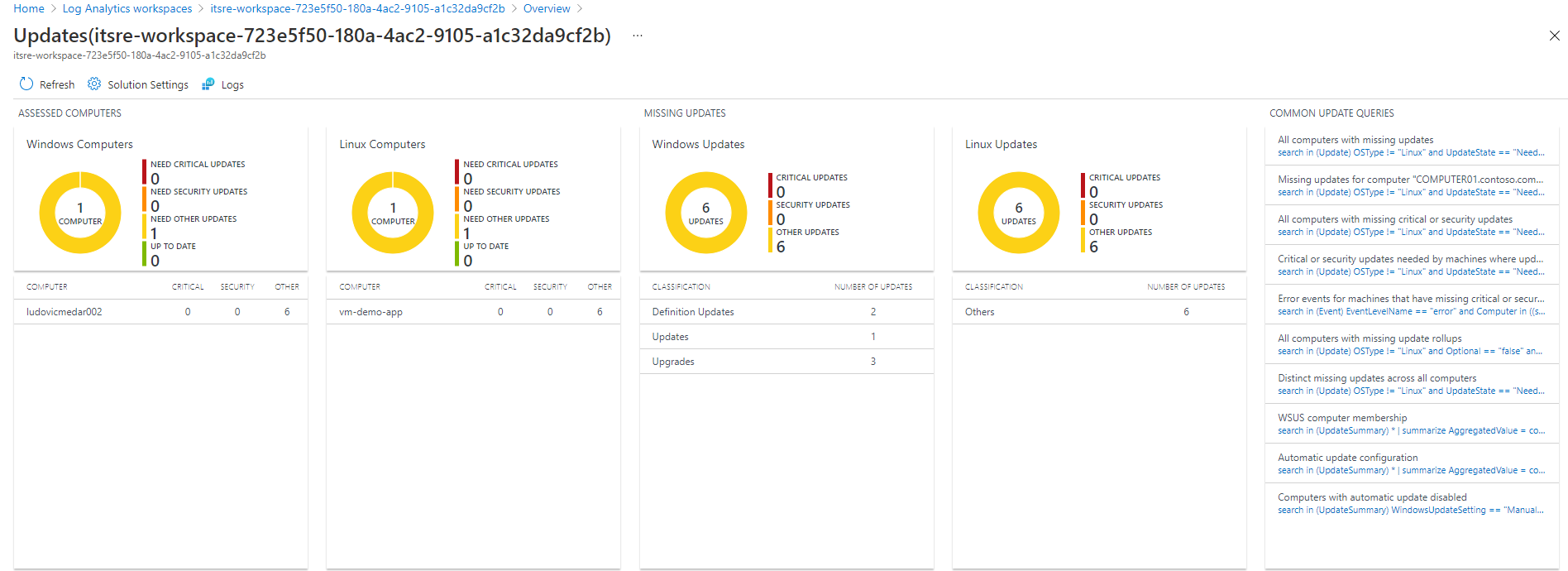
Track missing updates that need to be deployed (Windows and Linux)
Virtual machines connected to the Update Management solution automatically send the list of updates that need to be applied on a periodical basis (depend on operating system). We can track missing updates using Azure Automation update management solution using the "Missing updates" tab as illustrated below:
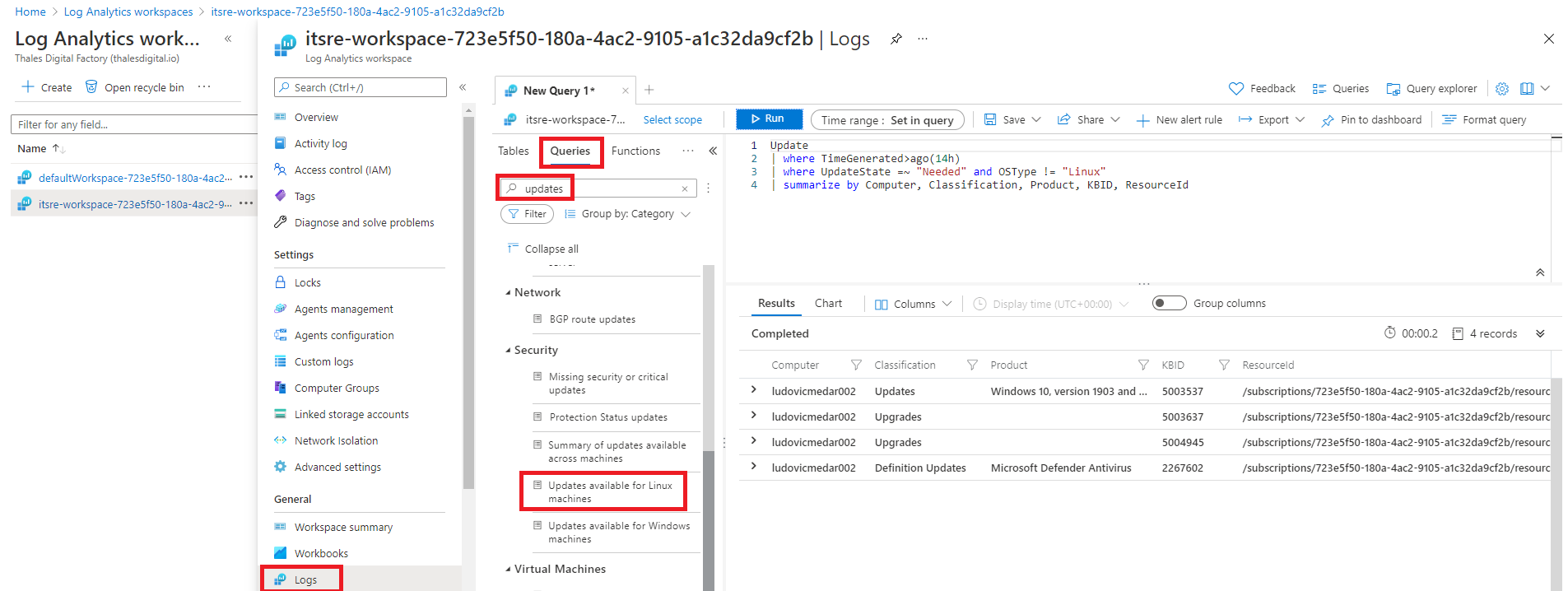
At Azure Log Analytics Workspace level, we can rely on the following tables to perform advanced search:
- Update
- UpdateSummary
Azure Log Analytics workspace already provide a set of Kusto queries to perform requests on theses table. Just click on the "Logs" then "queries" and filter with the "updates" keyword to find related queries. In illustration bellow, we track updates that appear as available for Linux based operating systems in a fourteen hour time frame.
Organize deployment of updates using deployment schedules
Update Management solution allow to organize update deployment using deployment schedules. A deployment schdule target a single type of Operating System (Windows / Linux) and allow to:
- Filter virtual machines to be processing using dynamic groups or using a fixed list of virtual machines
- Filter updates based on classification (security, critical, ...)
- Manage when the operation will be performed (one or recurring)
- Manage reboot scenarios (Reboot if required, never reboot, Always reboot, Only reboot without installing updates)
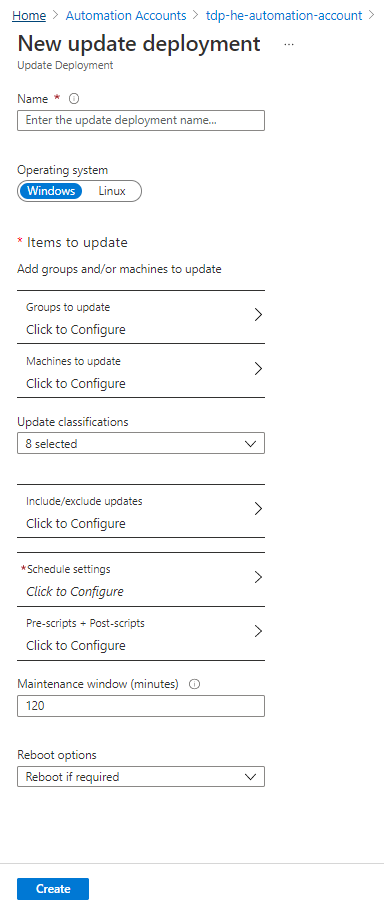
In illustration below, we created a deployment schedule that targets a single windows virtual machine to perform both update and reboot operating. This deployment schedule will be run once in a near future after creation.
Because filtering a fixed list of virtual machines is not efficient, we can manage a dynamic list of Virtual machines based on groups as illustrated below:
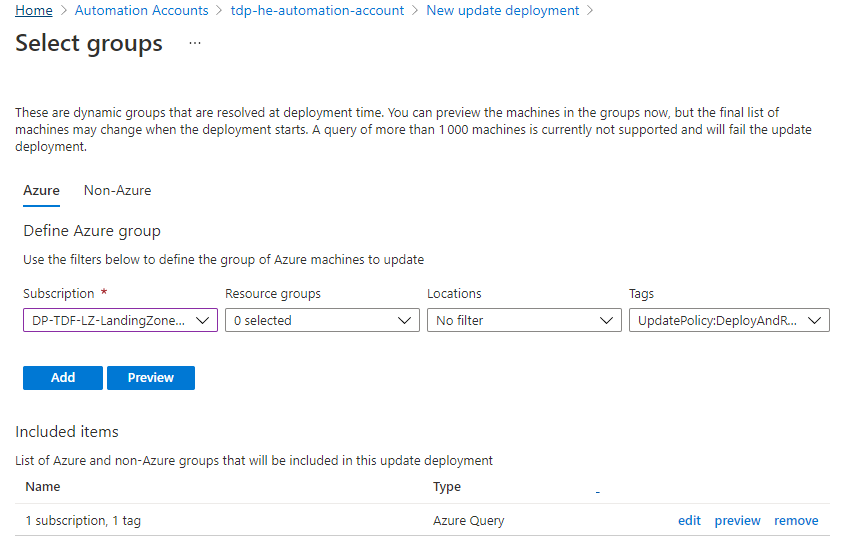
In this configuration, we used a tag configured at virtual machine level. If tag match (key and value), virtual machine is considered as member of the group. With such approach, there is no need to update the deployment schedule for each new virtual machine.
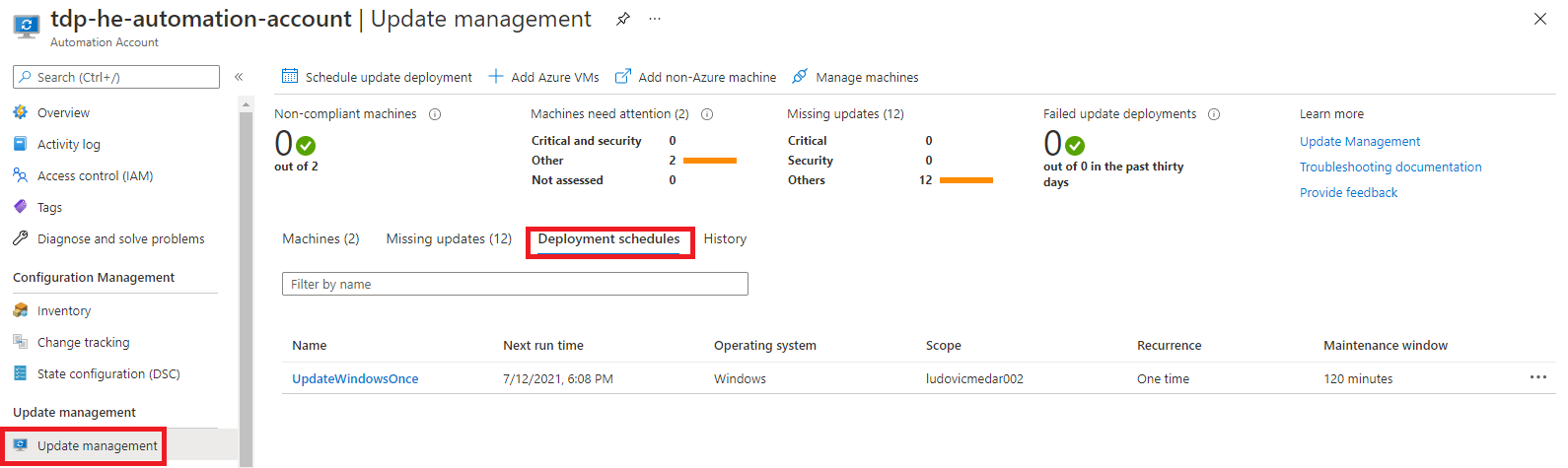
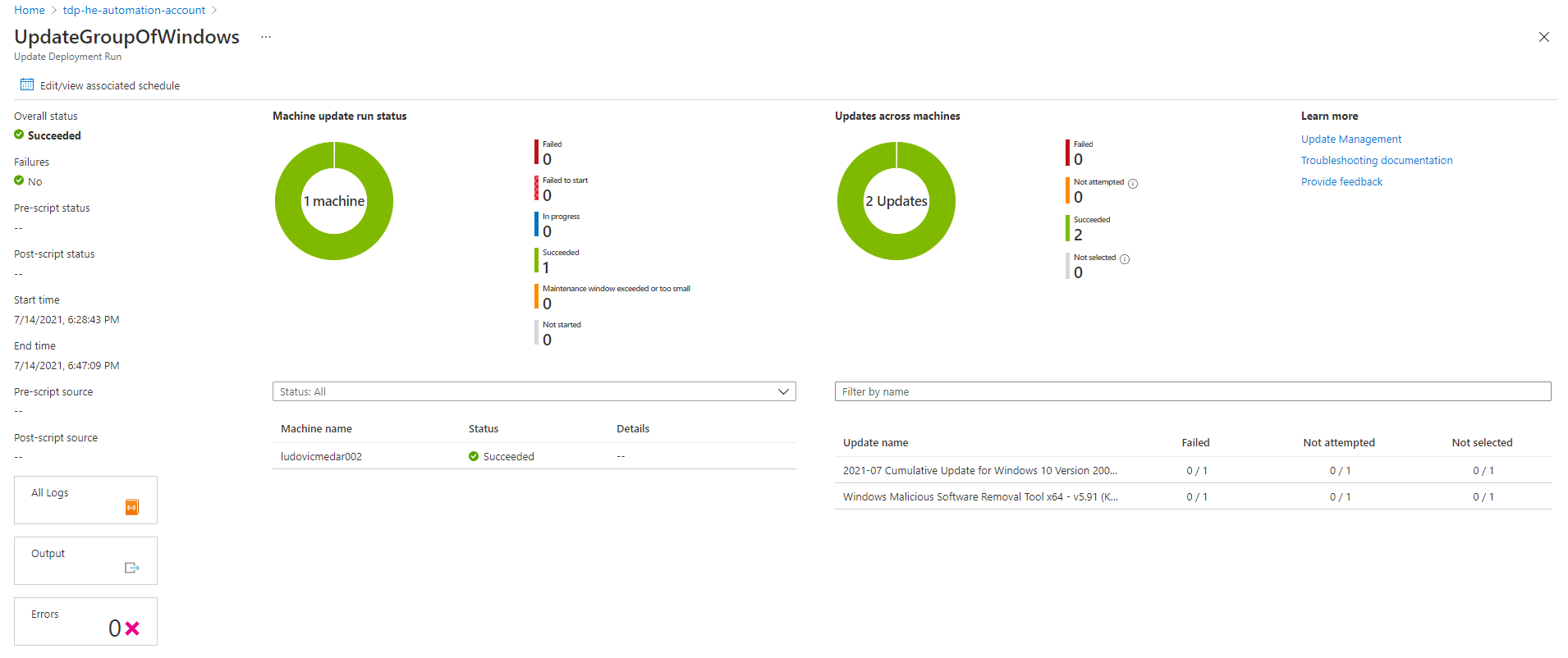
We can track schedule status using the history tab as illustrated bellow:
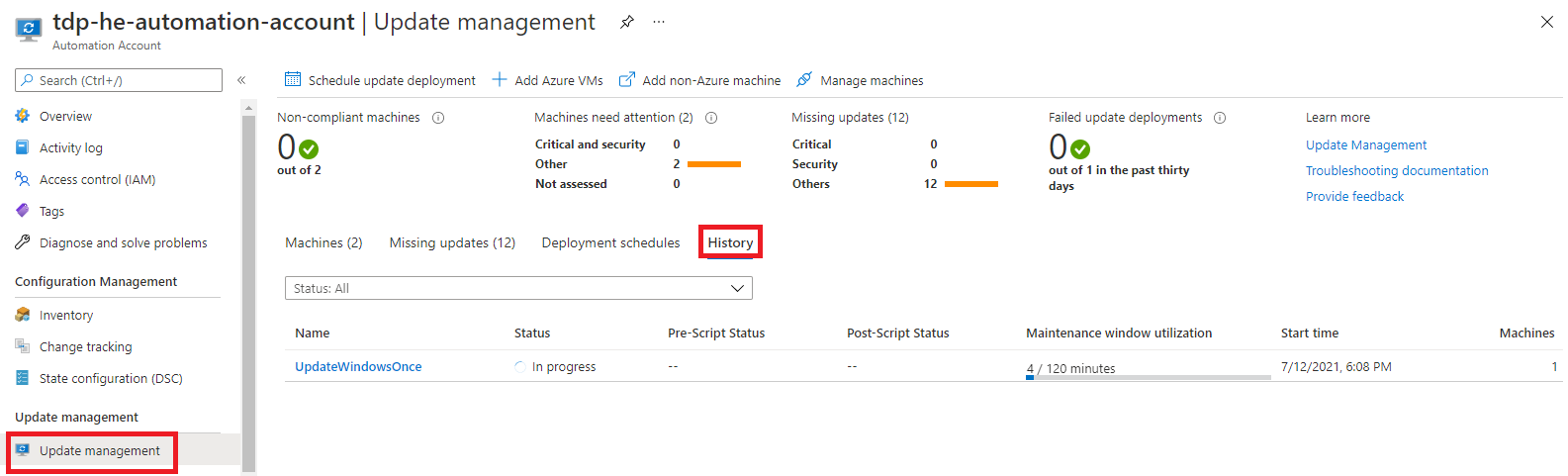
Once a schedule is completed, we can access to the results of the operation. Bellow, we see that two updates successfully installed on a virtual machine.

Next time the virtual machine will report his patch management status, updates will be considered as installed. When querying the Log Analytics workspace, be sure to use the TimeGenerated attribute to filter the latest status reported.
How to use Log Analytics query to get the patch status of my virtual machines?
Every virtual machine connected to the Update Management solution, report his missing updates to your local Azure Log analytics workspace on a periodical schedule. For this reason, we can find multiples entries in the Updates Tables for the same virtual machine. Query bellow report number of missing updates organized per categories (critical, security, non-critical updates):
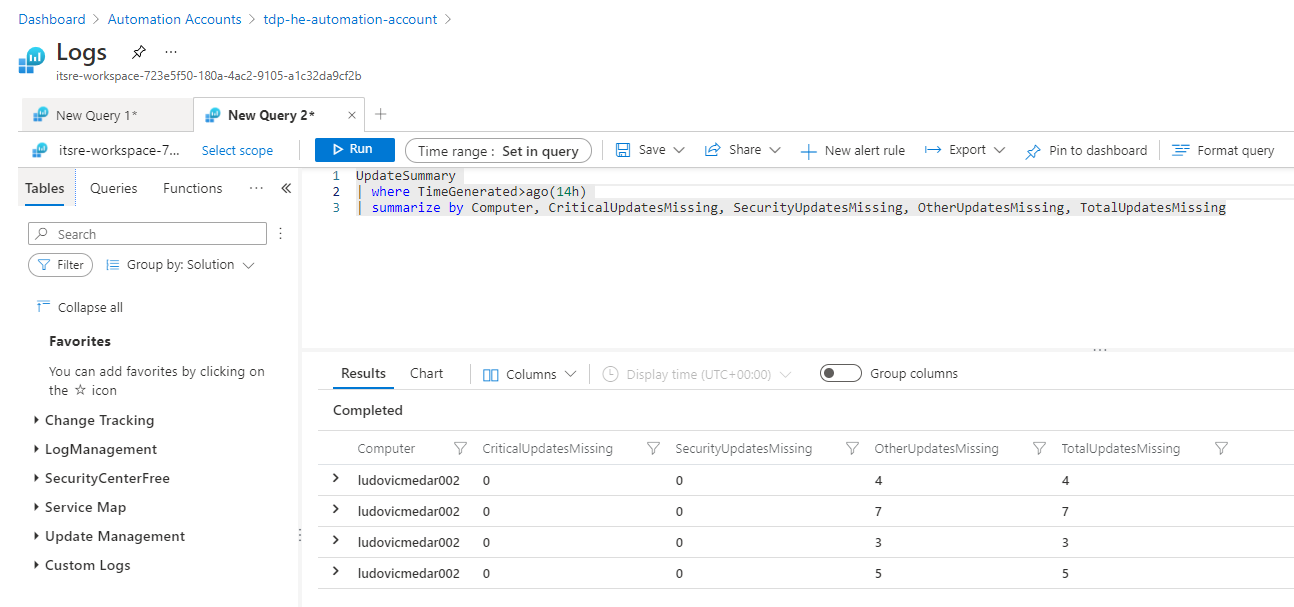
The result of this KUSTO query can be used to create an alert rule and even presented in your custom Azure dashboard.
Track the deployment schedule status over the time
Deployment schedule status is available in the history tab as illustrated below:
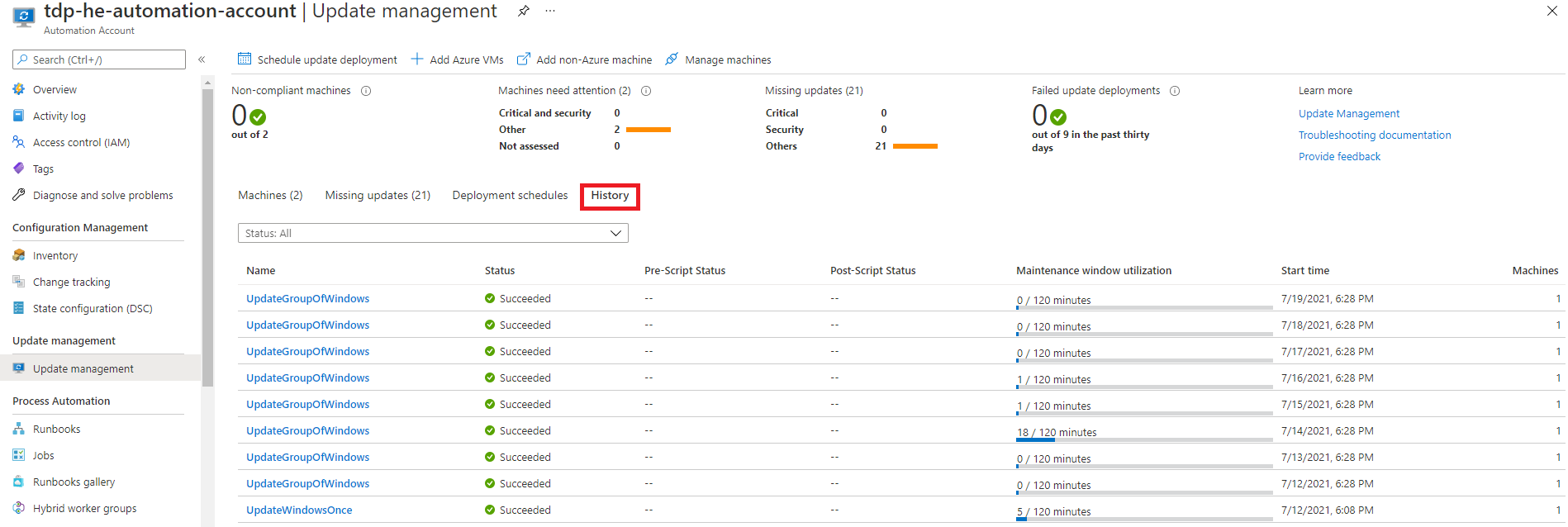
For each execution of the deployment schedule, we can track what updates were installed, if it was successful or not.
FAQ
How to perform software inventory?
Change Tracking and inventory solution is automatically configured by default. It is available in the same Azure Automation Account as illustrated bellow:
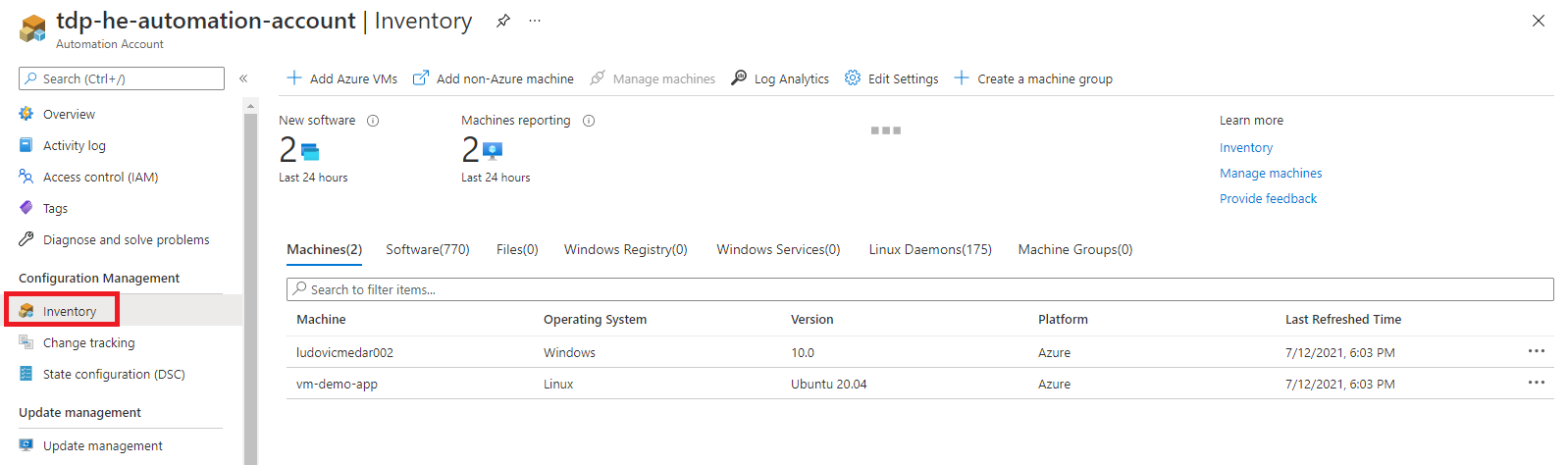
By default, solution is only configured for inventory services, targeting all virtual machines in your subscription. You can configure inventory settings by yourself.