Corporate Addon
Introduction
By default, the infrastructure landing zone is exposed to internet facilitating the interaction with your users and partners. Indeed, the cloud pushes our developers and architects to switch from a network isolation pattern to an authentication everywhere pattern. All our cloud resources are integrated to an internal azure active directory where all users are multifactorial authenticated (credentials + microsoft authenticator with laptop compliance for specific use cases).
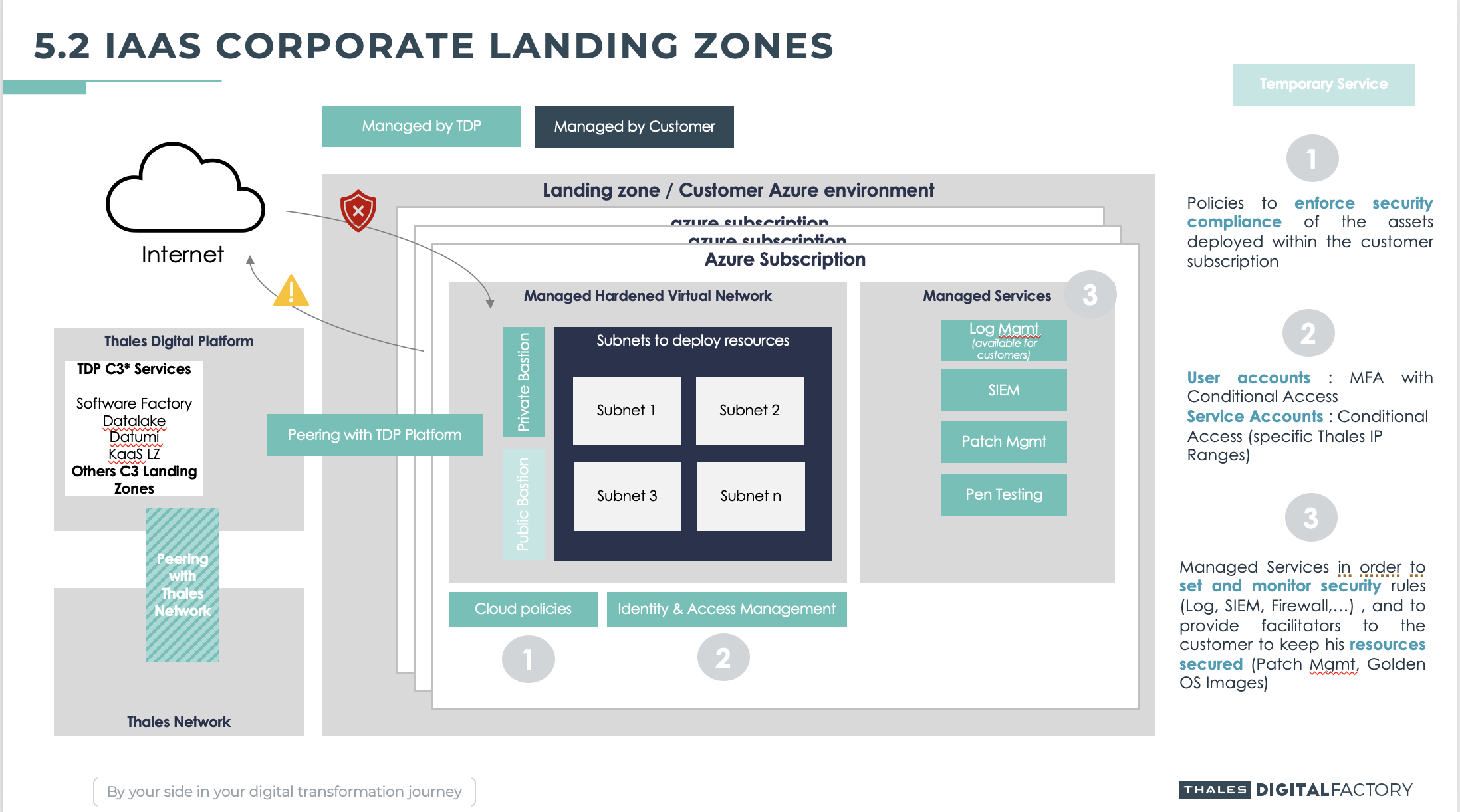
The Corporate Addon is designed to enforce network configuration to forbid any Internet exposition, and allows connections to and from the Thales Network (RIE). You may use it if :
- You don't need Internet exposition and you don't want the risk of misconfiguring something within your Landing Zone
- All of your users are using a Corporate Laptop connected to the RIE
- The Data sensitivity requires to forbid Internet Exposition
Note that Internet exposition is forbid but, outbound connections to Internet are authorized through the TNP Firewall.
Warning / known limitations:
- The corporate addon can be enabled only at the creation of the environment.
- The corporate addon cannot be disabled
- The end-users access is only limited to corporate networks (with a corporate laptop)
corporate laptop* : business networks or laptops are not considered by the Security System Information team as a corporate environment. No exception will be given
Comparison with standard service offer
| C3 LZ (Corp Addon) | C2 LZ (without Corp Addon) | |
|---|---|---|
| Internet Access | Inbound | Inbound |
| - Denied by default | - Allowed from all Internet on 443 / 80 | |
| - Requires Thales compliant device (TNAP, Thales W10) | - Allowed from a specific Internet IP on every other port | |
| - Can connect from everywhere in the world (Export Control => Can be limited with Conditional Access with geo-location and device compliance) | (the goal is to prevent admin ports exposed on all Internet) | |
| - Go through Azure Firewall managed by IT Network | - Every Inbound Internet connection is disabled by default when creating an Azure except for Azure Web Applications, but can be enabled by the client. | |
| Outbound | Outbound | |
| - No Limitation: Azure Firewall is not configured for outbound flow => IT Network responsibility (Export Control => See with IT Network if Outbound control is a possibility) | - No Limitation | |
| Access from/to others Landing Zones & Core Services | ||
| - Allowed to C3 Core Services | - Allowed through Internet | |
| - Denied to others C3 Landing Zones by default (must be enabled at Landing Zone level by the client AND IT Network at vWAN level if needed) | - Disabled by default (except Web Application for inbound). Can be enabled by the client himself | |
| => Accessed through Azure Virtual WAN (Internal) |
Corporate addon accesses
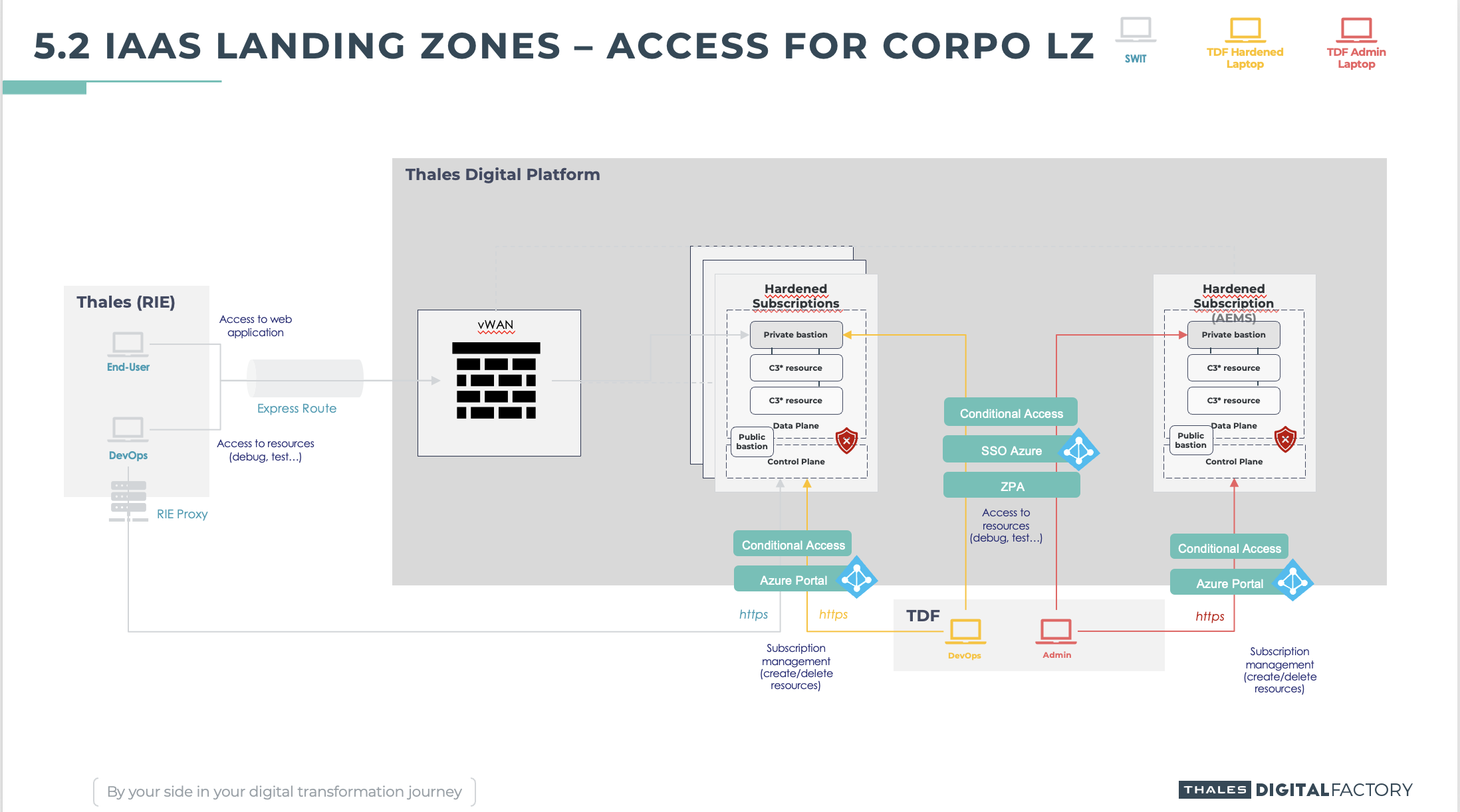
Description
Azure IaaS+PaaS supported
- Virtual Networks
- Public IP
- Load Balancer
- App Gateway
- App Services
- Virtual Machines
- Storage Account (All usages)
- Key Vault
- PostgreSQL
- Maria DB
- Cosmos DB (All usages)
- Azure Security Center
- API Management
- Databricks (On demand - admin deployment required)
How does it work ?
In a nutshell, Azure policies are applied to your Landing Zone in deny mode on the following topics :
- NSG rules that allow
inboundconnection from an Internet IP. - SKU for Load Balancers and Public IP are set to
Standardin order to force the usage of NSG. - PaaS services are required to use a Private Endpoint to be accessed to.
- PaaS services requires you to deny Public Access to each one of them.