Encrypt my data using Confidential Addon
Context
From Q3 2023, Trustnest infrastructure landing zones provide a way to use Thales CipherTrust provided by Thales CPO to manage your encryption keys.
The purpose of this documentation is to show HOWTO use CipherTrust Manager with a concrete use case: the encryption of an Operating System disk.
If the Confidential Addon is new for you, please have a look to the Cloud Act Risk Reduction on Public Cloud
CipherTrust Portals & URL
CipherTrust Manager for standard environment: https://ciphertrust.ahe.thalesdigital.io
CipherTrust Manager for corporate environment: https://ciphertrust.tdp.infra.thales
Prerequisites
- You should first have an infrastructure landing zone (with or without the Corporate Addon). Subscribe to iaas lz
- You should ask an access to CipherTrust using a generic request
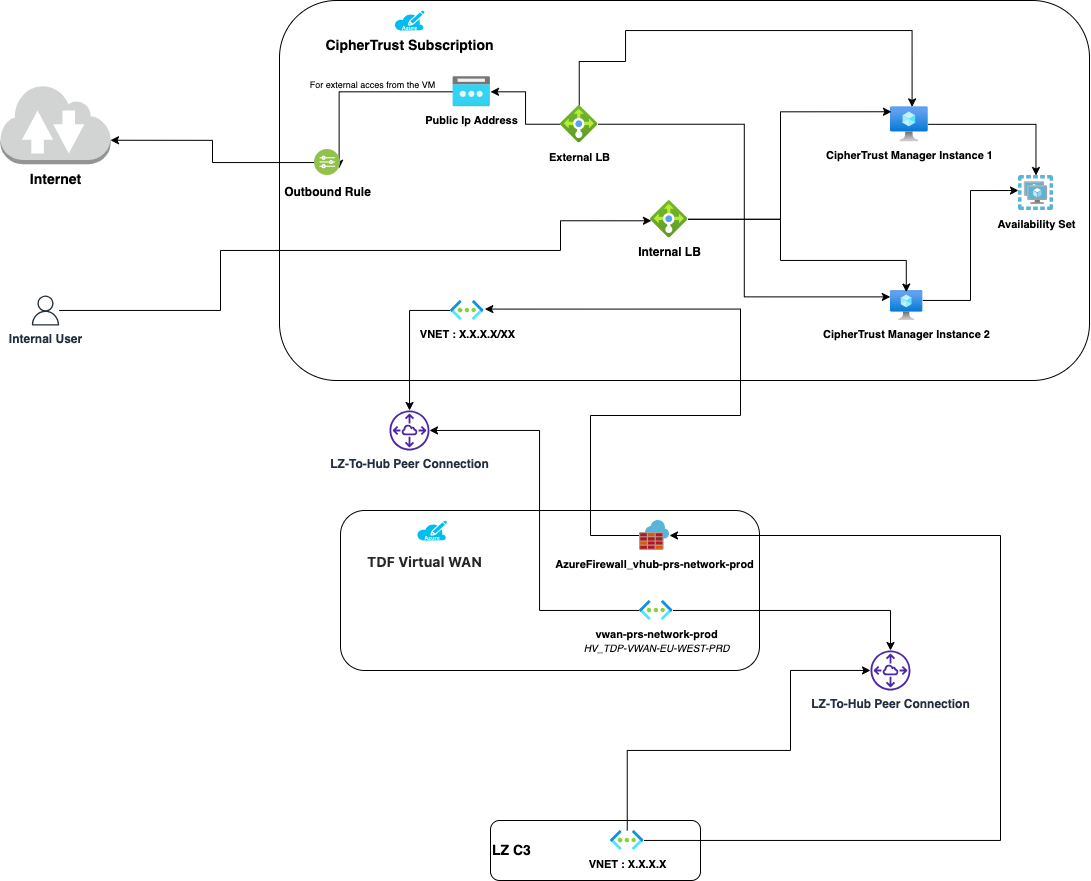
Architecture
For corporate environment:
Features
- CipherTrust Manager is deployed in High Availability
- CipherTrust Manager is backup frequently (1 time per day).
- The keys managed by CipherTrust Manager in the customer "domain" are aso backup (1 time per day).
HOWTO encrypt an OS disk with CipherTrust ?
Create a Keyvault
-
Request or create a KeyVault inside the client's subscription
-
Add Key Vault Administrator role on the Keyvault for the App or add an access policy with all rights on Secrets, Keys and Certificates for the App
- Key Permissions
- Backup
- Create
- Delete
- Get
- Import
- List
- Purge
- Recover
- Restore
- Update
- Release
- Rotate
- GetRotationPolicy
- SeRotationPolicy
- Secret Permissions
- Backup
- Delete
- Get
- List
- Recover
- Restore
- Set
- Purge
Configure the connection between Ciphertrust and the Landing Zone
- Connect on CipherTrust Manager with the user's credentials and switch to the client's domain
| Environment | URL |
|---|---|
| Production | https://ciphertrust.tdp.infra.thales |
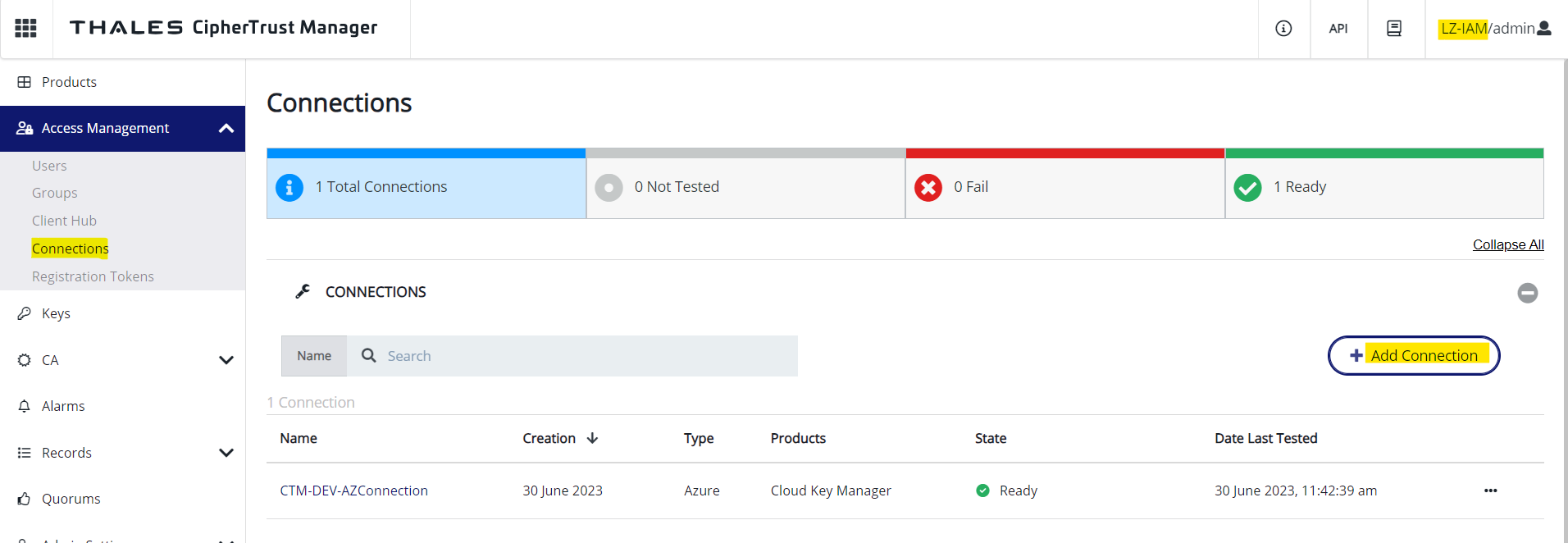
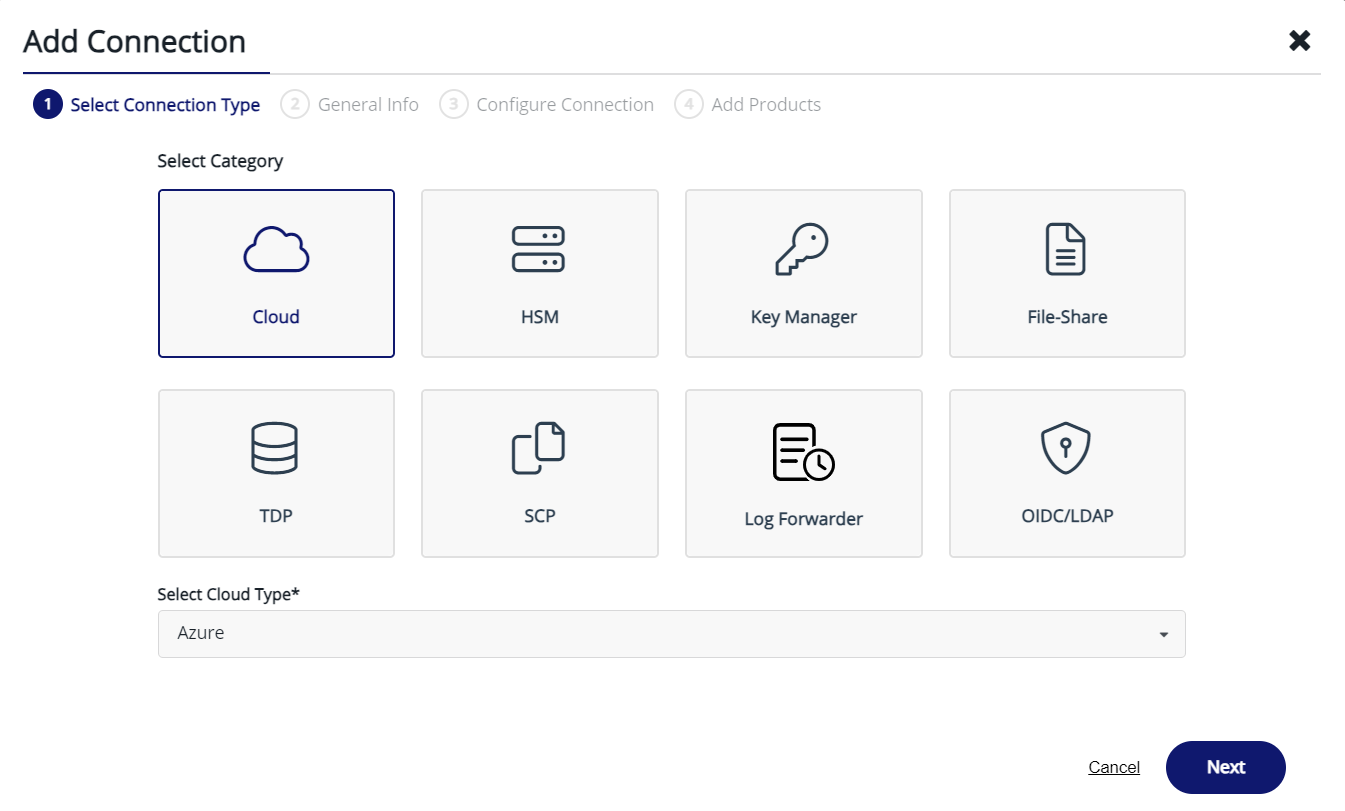
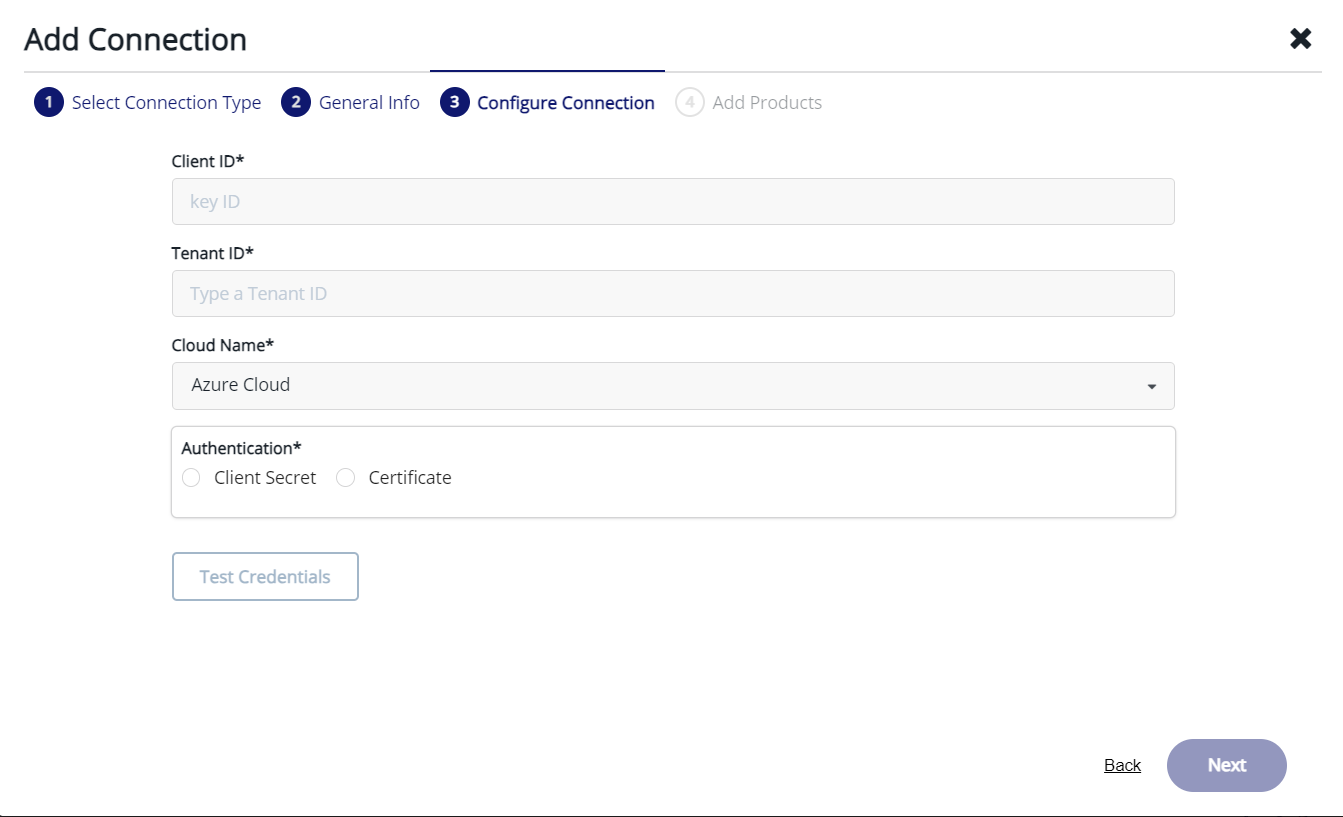
- Add a connection to the client's Azure Subscription by entering those informations
- App Client Id ==> newly created App ID
- Example LZ-IAM DEV ==> b7449bf5-77f5-4f98-98bf-0be283051a9c
- Example LZ-IAM PROD ==> 3a131c96-eb57-4af3-a981-b3e88daaecc2
- App Tenant Id ==> current Azure AD tenant ID
- TenantID ==> 737c6905-f186-4bcf-afb3-43e349ee23a3
- App Client Secret ==> newly created App secret
- Landing Zone Subscription Id or Name ==> client's subscription ID
| Environment | URL |
|---|---|
| Production | https://ciphertrust.tdp.infra.thales/#/console/access-management/connections-management |
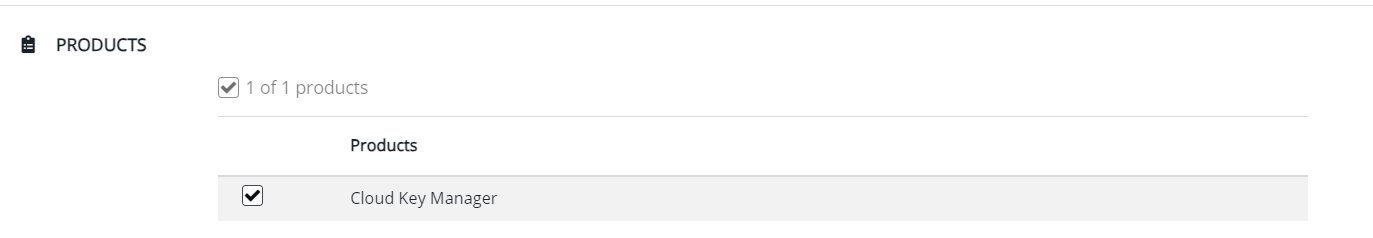
- Select "Cloud Key Manager" product when creating the connection
Configure Cloud Key Manager
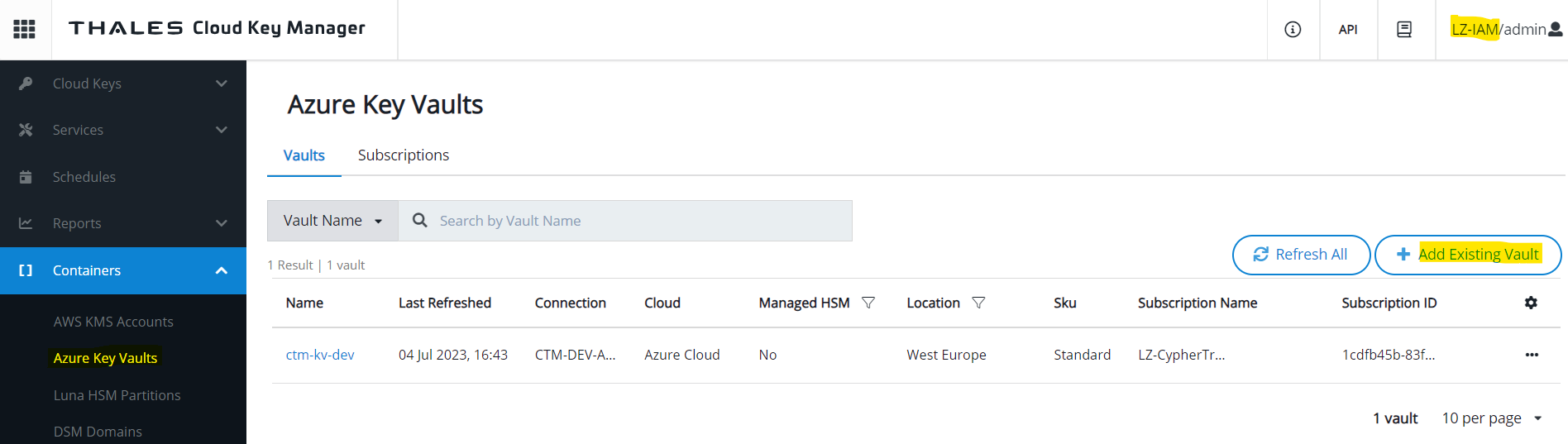
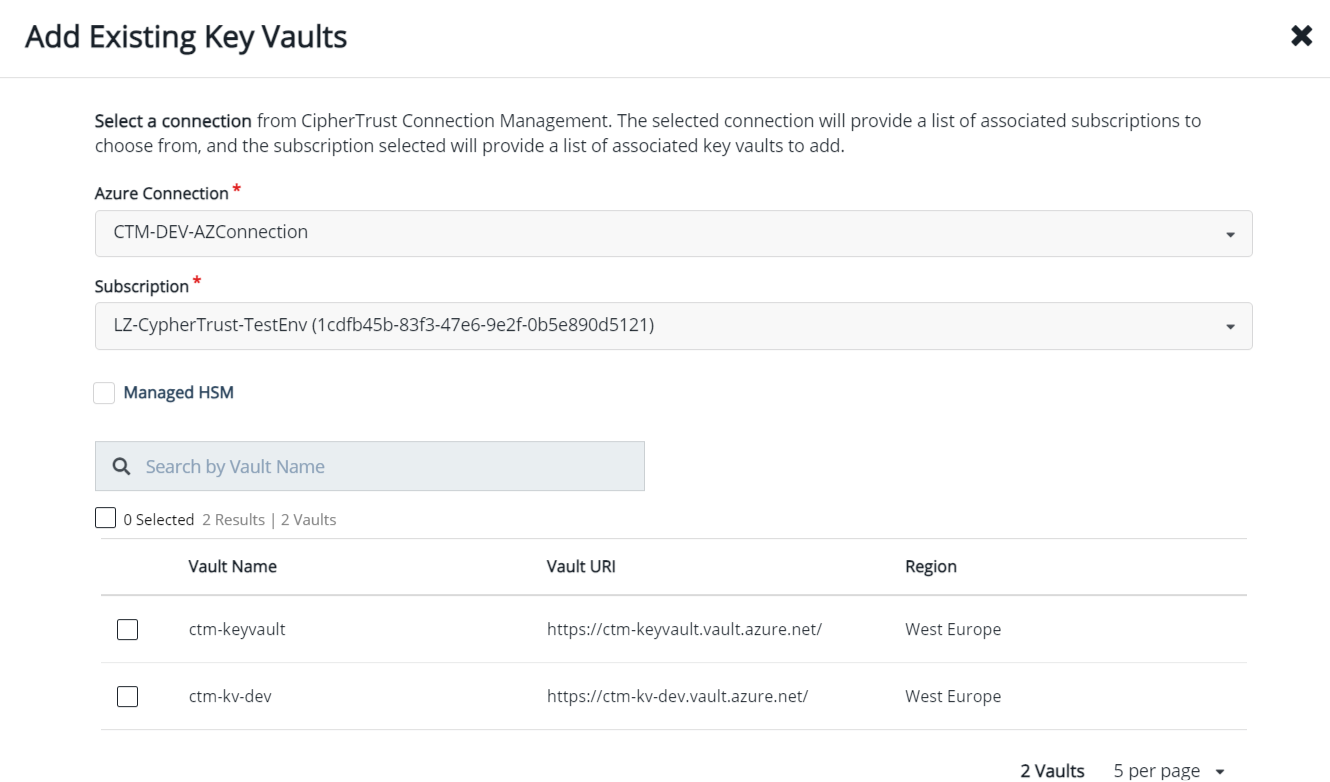
Add connection to an existing Key Vault
- Still connected with the same client user, add an existing Key Vault in Ciphertrust Manager
| Environment | URL |
|---|---|
| Production | https://ciphertrust.tdp.infra.thales/#/cloud-key-manager/settings/azure/vaults |
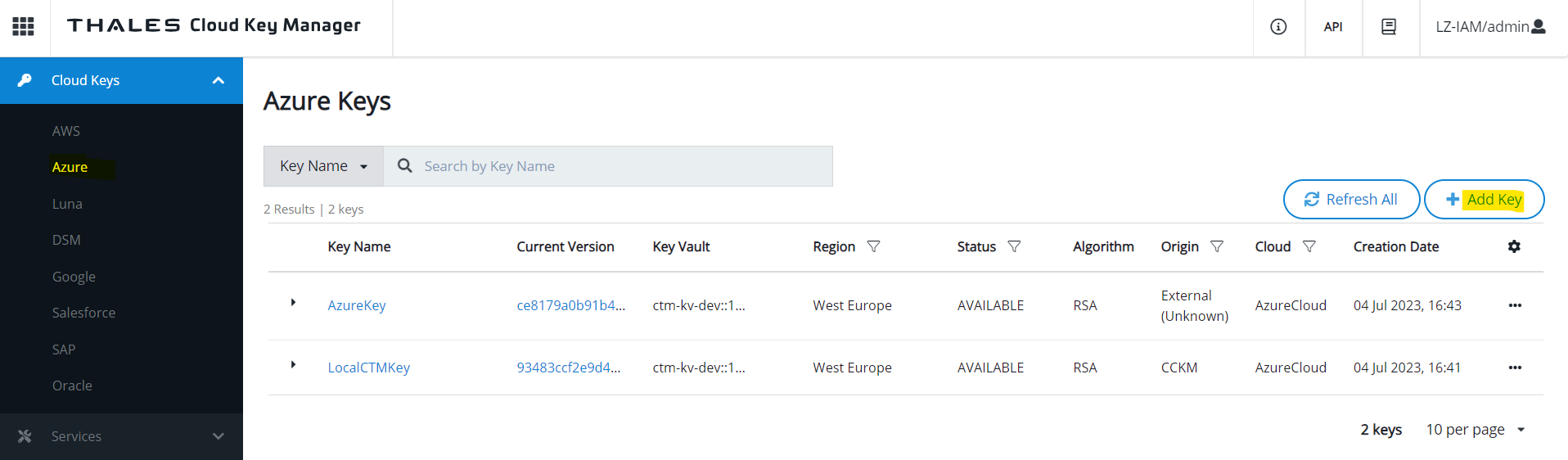
Create a Cloud Key
You can now add a Cloud Key managed by Ciphertrust in the Keyvault
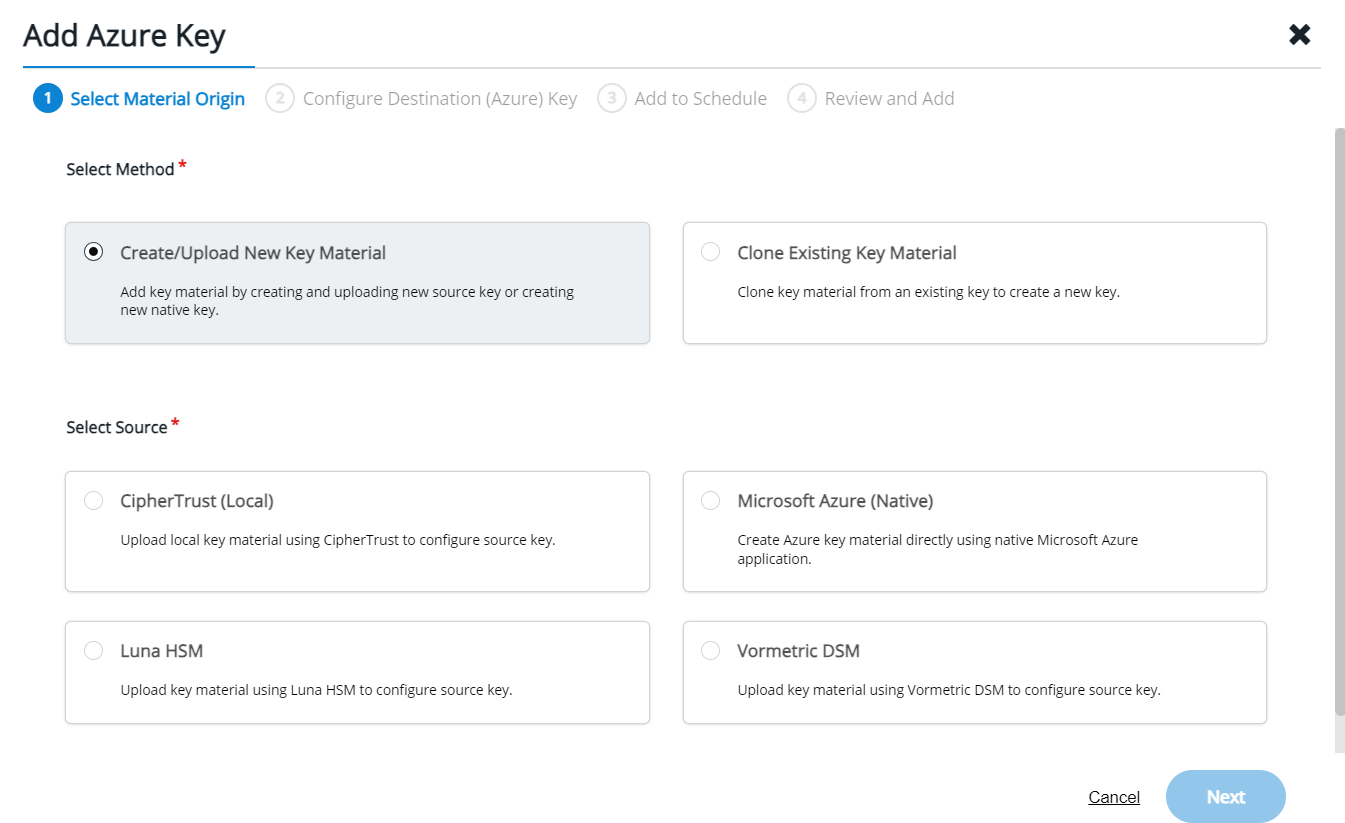
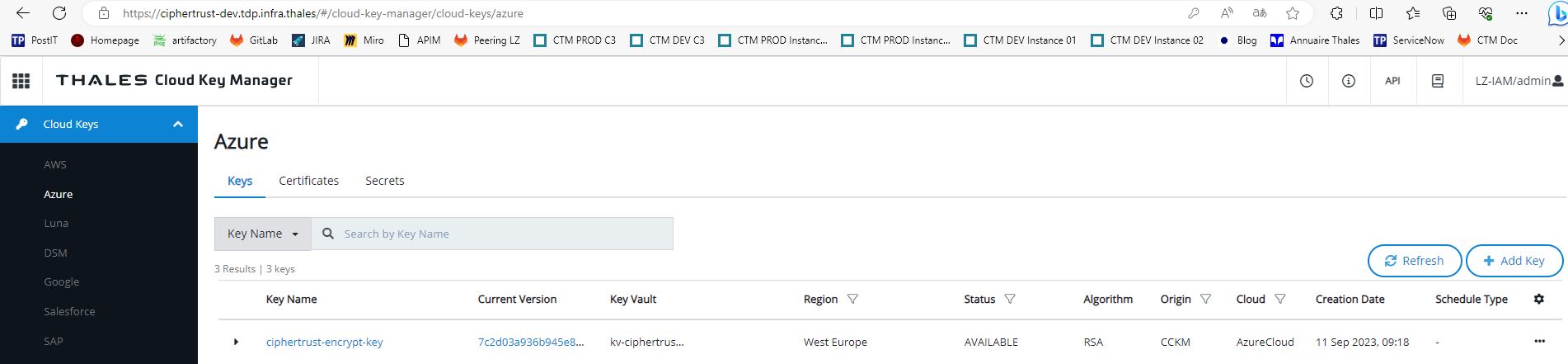
| Environment | URL |
|---|---|
| Production | https://ciphertrust.tdp.infra.thales/#/cloud-key-manager/cloud-keys/azure |
Create a disk encryption set
-
Go to the Azure Portal (or use AzureCli to connect the client's subscription)
-
Create a "Disk Encryption Set"
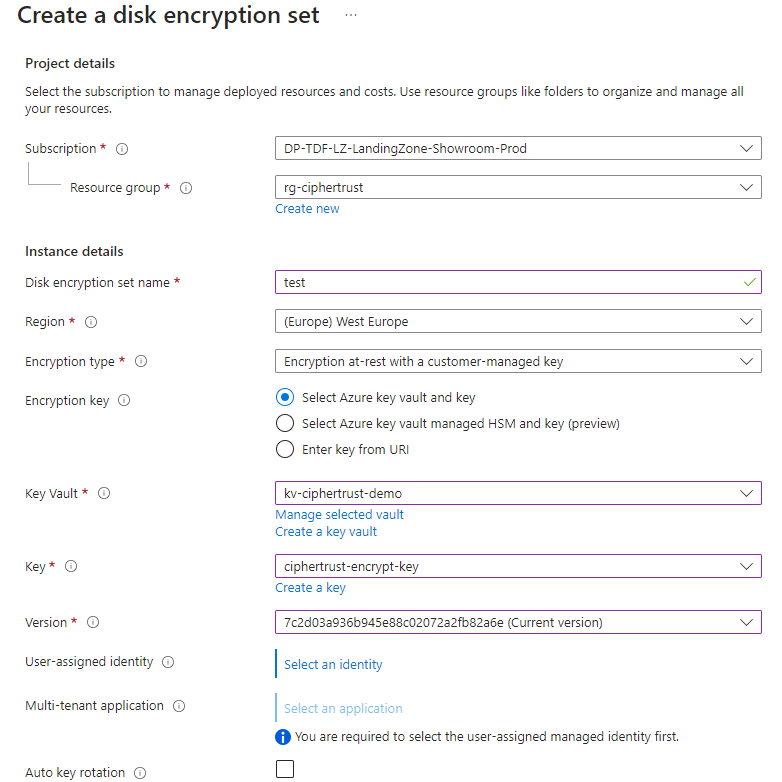
- Subscription ==> client subscription
- Resource Group ==> resource group where you want to create the disk encryption set
- Name ==> disk encryption set Name
- Region ==> client subscription Region
- Encryption Type ==> select **Encryption at rest with a customer-managed key**
- Key Vault ==> select the client key vault
- Key ==> select the previously created key in Customer
- Version ==> select the version of the previously created key
- Click on "Review and Create" and then "Create"
Add rights on KeyVault for Disk Encryption Setup
- Create an "Access Policy" to allow the previously created disk encryption set access to the key vault
- Key Permissions ==> Get, Wrap key, Unwrap key, encrypt
- Secret Permissions ==> Get
- Certificate Permissions ==> Get
Create a Virtual Machine with disk encrypted
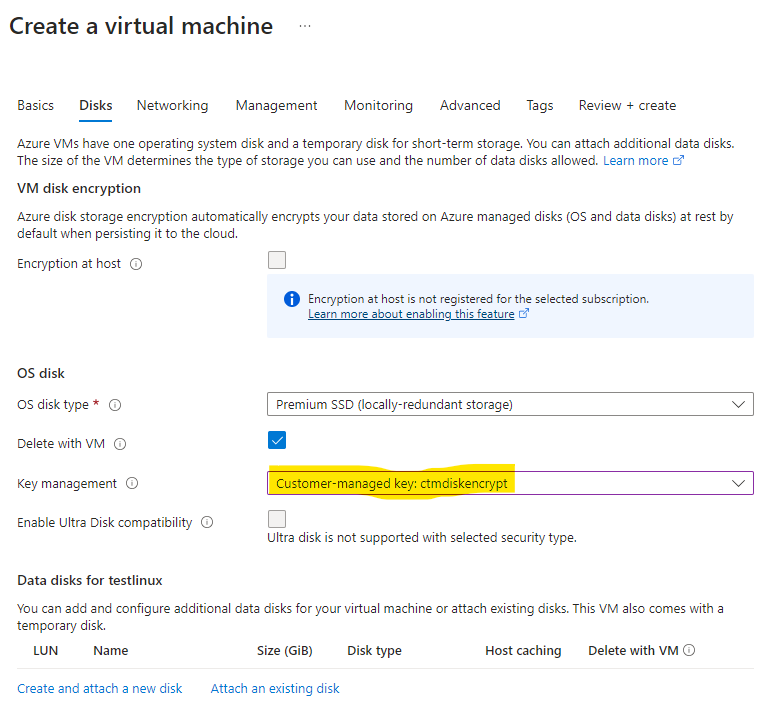
- Create a virtual machine on the client's subscription which will use the previously created disk encryption set to encrypt its disk(s)
On the "Disks" tab, under "Key Management" select the disk encryption set
-
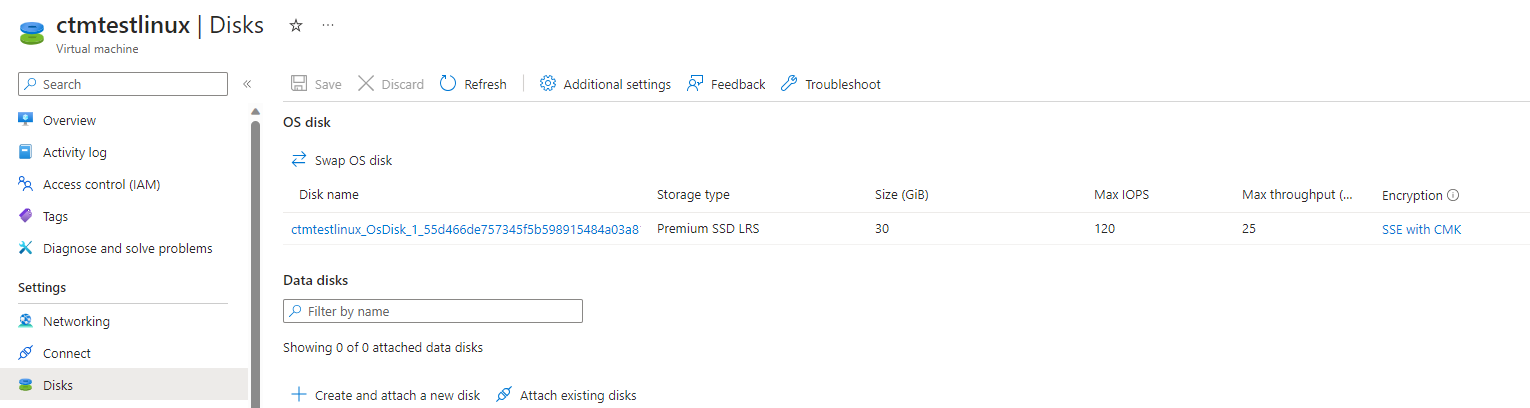
After the creation, you can go on "Settings" blade of the virtual machine and select "Disks"
-
On the "OS disk", you can see a column "Encryption"
-
Click on "SSE with CMK", you'll be redirect to the previously created disk encryption set