The Use case
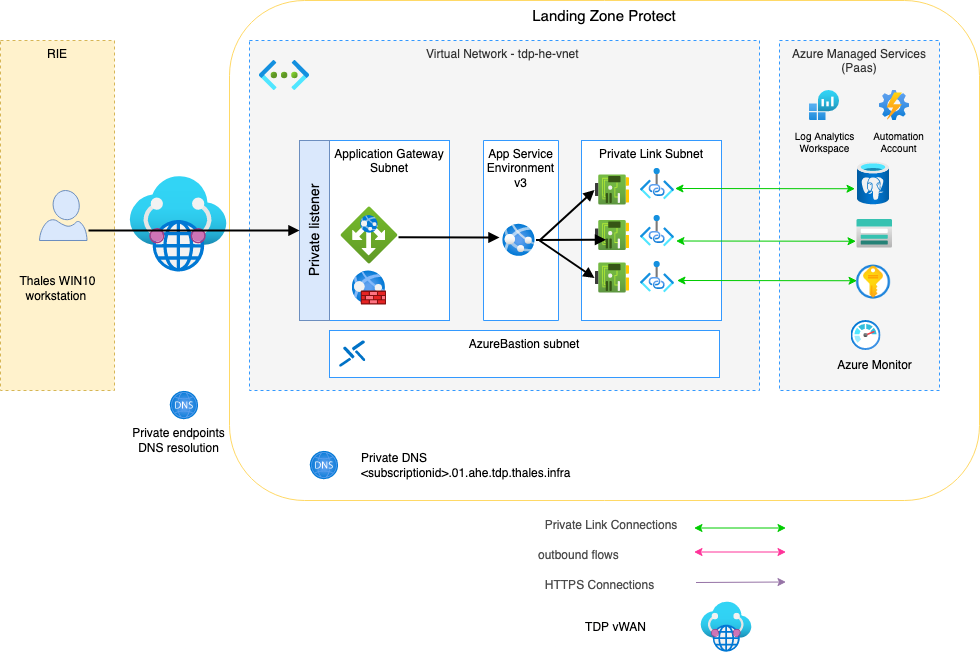
On top of a Protect Landing Zone, you need to build the infrastructure to host an application accessible from the Thales RIE using Thales Win10 workstation. The application will be behind an Application Gateway with a private listener. The application will consume various Azure managed PaaS services such as:
- a PostgreSQL database
- a Keyvault for storing application certificate and database credentials
- a storage account for your application static files
Every service will be accessed by the application through a private link rather than over the public network. To ensure the security of your application, you will also enable WAF on the Application gateway.
You will need at least a network L size to host a minimum /27 subnet that will be dedicated to App Service Environment.
Constraints
Exposure
Reachable privately by the applicatiion only:
- PostgreSQL database
- Keyvault
- Storage account
Reachable from Thales RIE networks only through a private gateway:
- Application
Application Gateway
- When deploying the Azure Application Gateway (Deploy Azure Application Gateway), choose either WAF_V2 or Standard_V2.
- From the Backend settings, select "https" as the Backend protocol. In "Trusted root certificate" section, the backends must be in the allowlist of the application gateway. Upload the public certificate of the backend servers to this Backend setting.
App Service Environment
- version: it needs to be App Service Environment v3
- network size: It needs to run on a dedicated subnet of minimum size /27 (32 addresses)
- Virtual IP: the endpoint needs to be an internal load balancer because your applications should not be reachable over public internet
- TLS version: the minimal allowed version must be 1.2
- TLS ciphers: the application service environment needs to be configured with strongest TLS Cipher suites: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 and TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256."
Application Service Identity
For your application service to access Keyvault, you may want to use a managed identity (user or system)
Application Service
- In Diagnostic settings, configure for sending logs to the Log Analytics workspace of the Landing Zone.
- To ease and secure access to the database connection string, you can store the corresponding Keyvault secret reference as a value of an application setting (or in specific cases as a value of a connection string). If you're unsure of the format, refer to Microsoft Azure reference documentation here. If you're unsure where to store it exactly, refer to this entry of Microsoft Azure reference documentation here
- Go to the https settings of the application service then enable https only enforcing TLS 1.2 as the minor TLS protocol.
Keyvault
- Access policies > Grant your Application Service access to your database credentials.
- Network Access > Create a private endpoint integrated to a subnet that doesn't contain the Application Gateway.
- Enable soft delete
DNS resolution
Each Protect Landing Zone is delivered with a private DNS zone (<subscriptionid>.01.ahe.tdp.infra.thales).
Custom DNS servers are deployed at the TDP level and when the landing zone is delivered to you, tdp-he-vnet network has already been configured with them.
Private DNS Zone
This DNS zone contains entries to be resolved within the virtual network tdp-he-vnet.
- You may want to create an additional private DNS zone with a shorter and friendly name. Refer to the page here to know more about it.
- Virtual Machines will register automatically in the private DNS Zone.
- Internal Load Balancers require their DNS records to be manually added to the DNS zone
Thales Internal DNS resolution (*.corp.thales)
- For your application to access to a Thales Internal service from your Landing Zone
- For the Thales users to access to your application from the Thales RIE
*.corp.thales DNS resolution will rely on our own DNS servers that will relay requests to Thales.
Private endpoints case
For all the private endpoints you will need to connect Azure PaaS Services to the tdp-he-vnet virtual network, you do not have to create additional DNS zones since it will rely on existing Azure DNS zones out of the IaaS Landing Zone.
At the Private endpoint creation time, set "Private DNS integration" to "No". Integration to our DNS infrastructure is already in-place. Refer to our documentation.
The private endpoint creation will automatically be detected and trigger the DNS registration of the needed A record in our fully-managed private DNS zones. Thanks to this, DNS resolution of the private endpoints will also be possible from other subscriptions.
Certificate management
Refer to this page
PostgreSQL Server
- You need to select Flexible server
- Change "Deny public network access" to Yes.
- The PostgreSQL server will only be accessed from the web app. To achieve this purpose, you'll have to create a Private endpoint connected to services dedicated subnet.
- Enforce TLS 1.2 version as the minimum TLS version.
NSGs
- inbound traffic from Internet is blocked and it's not possible to expose on an Internet public address.
Troubleshooting
Consult Troubleshooting page