Microsoft Defenfer Enabled
Introduction
Microsoft Defender for Cloud provides integrated threat protection for your hybrid cloud environments. It helps detect vulnerabilities, provides security recommendations, and offers protection against attacks with features like endpoint detection and response (EDR). It integrates with Azure and other cloud services to enforce security policies.
However, it doesn’t replace other specialized security tools. For example, it doesn’t manage detailed network security configurations, identity governance, or provide exhaustive compliance reports. Microsoft Defender complements, but does not replace, traditional firewalls or advanced SIEM systems.
Within Trustnest infrastructure landing zone, few components of Microsoft Defenfer for Cloud are already deployed on your behalf. This agents are used to continuously collect information on activities and share alert to our SOC. In case of security incident (alert handled by an analyst and the anormal behaviour is confirmed), TDFaccountID owner are contacted as well as the security Partner filled in postIT. They'll do the coordination of the security incident resolution.
Use case
- Secure your workload
- Secure your data
- Be monitor & supervised by TDF
Microsoft Defender for Cloud in details
What are the resources that are by default monitored ?
In a context of infrastructure landing zones, here are the resources where Azure Defenfer is deployed:
- Virtual Machines with Microsoft Defender for Endpoint P1. (available since 0.1.26 release)
- Storage Accounts with Defender for Cloud (new feature from August 2024)
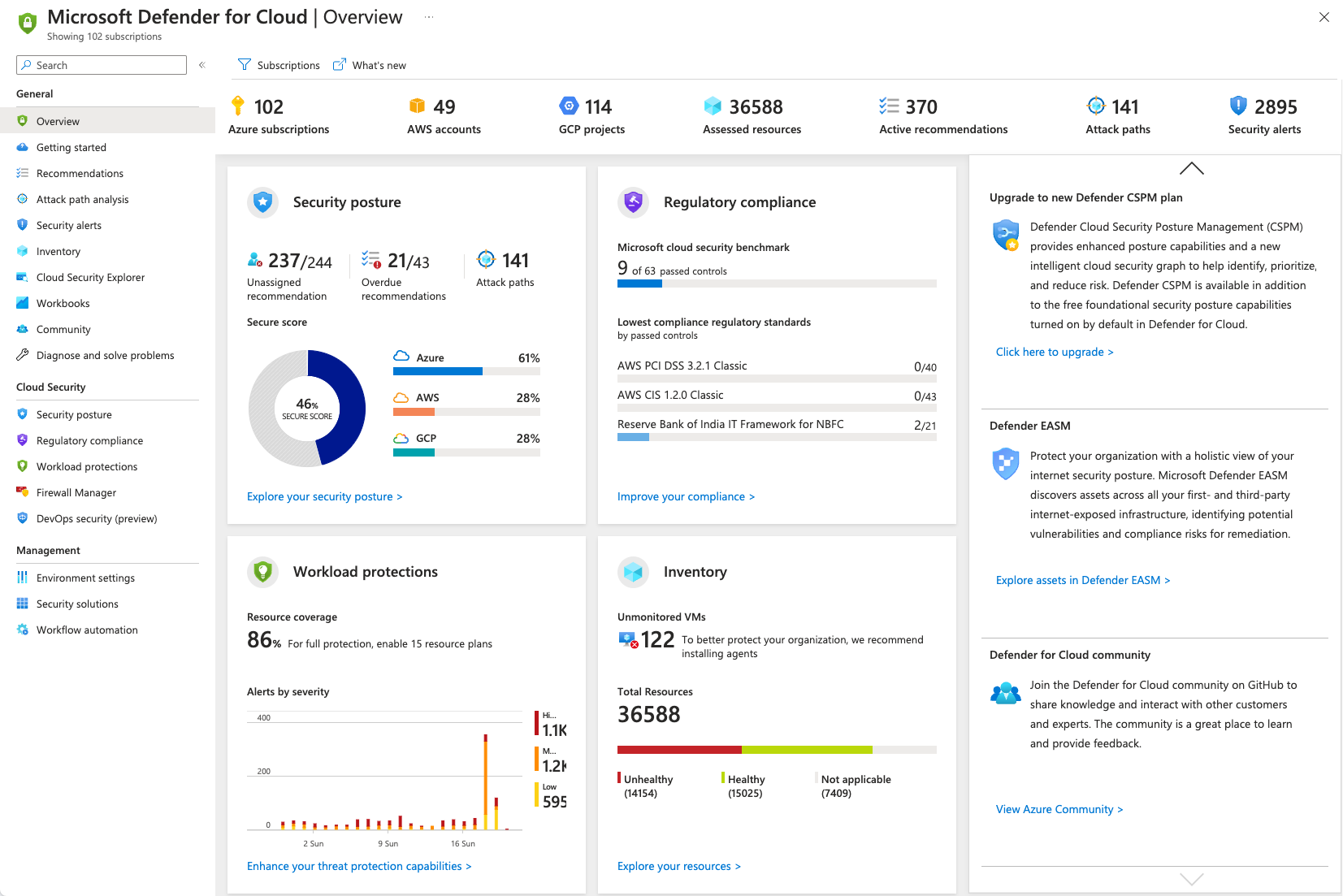
Is there any dashboard to get a 360 view (security) ?
Yes, Microsoft provides Microsoft Defender for Cloud | Overview
You should see:
How it works for Virtual Machines ?
Since release 0.1.26 of Azur Hardened Subscription relase, every virtual machine workload is automatically configured with Azure Defender for Endpoint antivirus solution. The solution is automatically deployed to your Azure Virtual machine as a Virtual machine extension. On a Linux virtual machine workload, extension is named MDE.Linux.
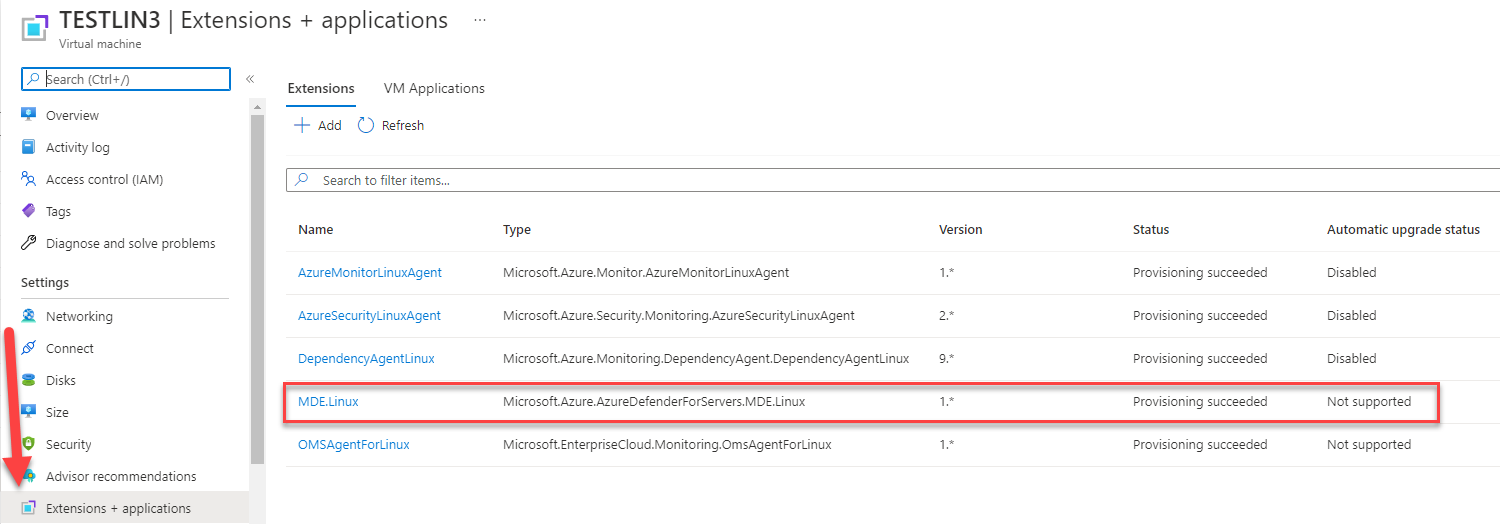
The deployment process is managed by Azure Policies. On your Azure Hardened subscription, an Azure initiative named [Preview]: Deploy Microsoft Defender for Endpoint agent. At time of writing this documentation, this initiative still in preview. So supported operating systems will evolve by the time. This Azure initiative include the following Azure policies that will be responsible to deploy Azure Defender for Endpoint to your workloads :
- [Preview]: Deploy Microsoft Defender for Endpoint agent on Windows virtual machines
- [Preview]: Deploy Microsoft Defender for Endpoint agent on Linux virtual machines
Theses Azure Builtin Policies does not cover all versions of Operating systems. Table bellow document Operating systems on witch Microsoft Defender for Endpoint is supported by Microsoft :
| Operating System | Version |
|---|---|
| Windows | 2008-R2-SP1 |
| Windows | 2008-R2-SP1-smalldisk |
| Windows | 2012-Datacenter |
| Windows | 2012-Datacenter-smalldisk |
| Windows | 2012-R2-Datacenter |
| Windows | 2012-R2-Datacenter-smalldisk |
| Windows | 2016-Datacenter |
| Windows | 2016-Datacenter-Server-Core |
| Windows | 2016-Datacenter-Server-Core-smalldisk |
| Windows | 2016-Datacenter-smalldisk |
| Windows | 2016-Datacenter-with-Containers |
| Windows | 2016-Datacenter-with-RDSH |
| Windows | 2019-Datacenter |
| Windows | 2019-Datacenter-Core |
| Windows | 2019-Datacenter-Core-smalldisk |
| Windows | 2019-Datacenter-Core-with-Containers |
| Windows | 2019-Datacenter-Core-with-Containers-smalldisk |
| Windows | 2019-Datacenter-smalldisk |
| Windows | 2019-Datacenter-with-Containers |
| Windows | 2019-Datacenter-with-Containers-smalldisk |
| Windows | 2019-Datacenter-zhcn |
| Ubuntu | 14.04-LTS |
| Ubuntu | 16.04-LTS |
| Ubuntu | 18.04-LTS |
Some operating systems are not yet supported, such as :
- Gen 2 versions of Operating systems (Linux & Windows)
- Windows 10 / 11 Operating systems (except if running Azure Virtual Desktop or Windows 10 Enterprise multi-session)
- Virtual machines images used by Network Virtual applicance
- Legacy CentOS, Red Hat, Debian, Oracle releases
- Microsoft client operating systems (already include an antivirus solution)
- Azure redhat Openshift related images
- Azure Databricks related images
Linux experience
In a Linux Virtual machine, you can manage Azure Defender for Endpoint antivirus solution using the mdatp health command as illustrated bellow :
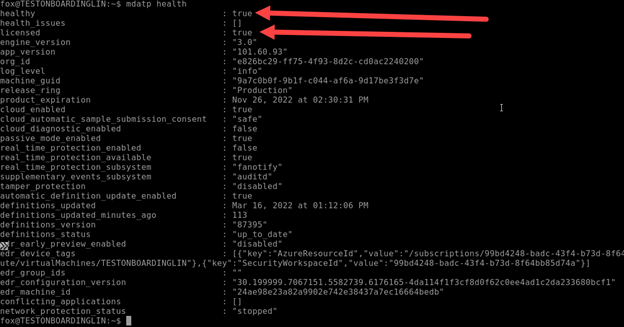
In result, you should be able to see that Microsoft Defender for Endpoint is healthy and licensed.
You can perform a manual scan using the mdatp scan command and have the following result:
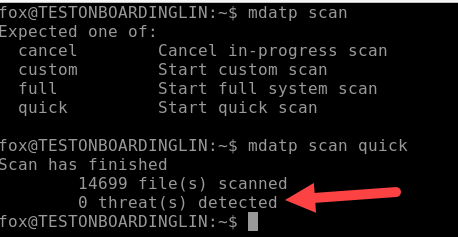
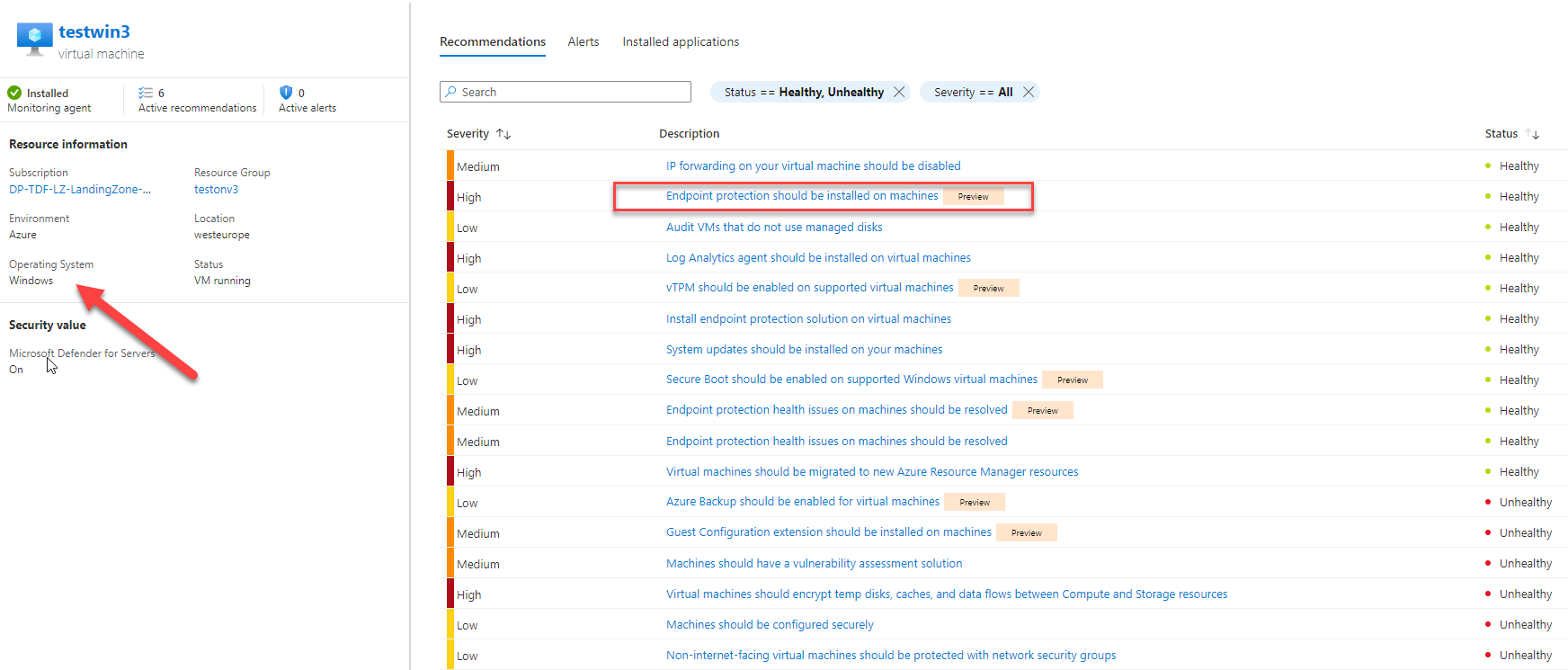
In Azure Defender for Cloud, your Linux virtual machine will comply with the Endpoint Protection should be installed on machines recommendation as illustrated bellow:
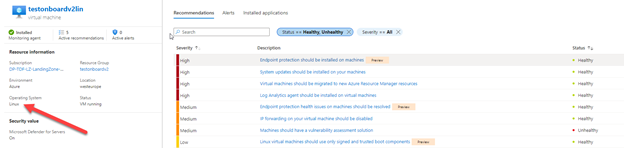
Windows Experience
In Azure Defender for Cloud, your Windows virtual machine will comply with the Endpoint Protection should be installed on machines recommendation as illustrated bellow: