How to use Private Endpoint / Private Link
This document aims to provide required information to use Private endpoint and Private Links.
Introduction
By Default an Azure PaaS resources is publicly available on Internet. PaaS resource exposition can be managed using Private Endpoints. Azure resources are linked to a Private Endpoint resource that connect it to a subnet on your Virtual Network using a network interface. Azure resources that are configured for Private Endpoint are no longer reachable from Internet, only from your Azure Virtual Network. Additional information can be found here
Azure Private Link is an extension to Private Endpoint that help you to expose your workload to be consumed using a Private Endpoint. Additional documentation is available here.
This document help you to use both Private Endpoint and Private Link services in the context of a C3 Azure Hardened subscription.
Prerequisites
Before creating your first Private Endpoint, some prerequisites must be considered :
- Private Endpoints support must be activated at Virtual Network level
- Dedicated subnet required for Private Endpoint
Private Endpoints support must be activated at Virtual Network level
By default Azure Virtual Networks does not support Private endpoints. Due to some Private Endpoints limitations, virtual network must be reconfigured as documented here Manage network policies for private endpoints.
This configuration can be performed by any TDF BL consumer having the following Roles in the C3 Azure Landing zone:
- Lead Developer
- Developer
Operation can be performed as described here Manage network policies for private endpoints.
Dedicated subnet required for Private Endpoint
At time of writing this documentation, Private endpoints are not yet compatible with Route table and Network Security groups. If you create a Private Endpoint on a subnet configured with tehses services, they will be disabled from the subnet. This could be problematic for some Azure services that rely them (AKS for example). Public preview is currently available in Azure :
- Public preview of Private Link UDR Support
- Public preview of Private Link Network Security Group Support
Until theses updates goes Generally available, recommendation is to create a dedicated subnet for your Private Endpoints.
Security considerations
Private Endpoint
When you create a Private Endpoint for a selected Azure resource, it establish a direct link. In order to make this link operational, you must approve the Private endpoint. Approval can be automatic (because you are the owner of the Azure resource or manual). Because a Private Endpoint can be linked to an Azure resource located in any Azure subscription even outside the TDF Azure AD Tenant scope, some security measures are enforced on C3 Azure Hardened subscriptions :
- Private Endpoints linked to Azure resource located in your C3 Azure Hardened subscription is allowed
- Private Endpoints linked to Azure resource located in a whitelisted TDF Azure Hardened subscription is allowed
- Private Endpoints linked to Azure resource not located in a whitelisted TDF Azure Hardened subscription is forbidden
- Private Endpoints linked to Azure resource not located in TDF Azure AD Tenant is forbidden
A custom Azure Policy is applicable to Private Endpoints objects in C3 Azure Hardened subscription will enforce theses rules. At current time the Private Endpoint whitelist include the following TDF Subscriptions :
| Azure Subscription Name | Azure subscription ID |
|---|---|
| TDP DataLake Gen2 C3 Production | 2d4dd519-5088-40af-96d9-85f2e70d9ed4 |
| TDP DataLake Gen2 C3 Dev/QA | a9e28d08-a884-4144-a7b4-3661d21a20fe |
| TDP DataLake Gen2 Prod | d7876be1-a0c5-4734-933d-bc6a6ae1b931 |
Private Endpoint resource created in your C3 Azure Hardened subscription are automatically approved. Private Endpoint created for resources located in whitelisted subscription list require approval from subscription owners to finalize configuration.
Private Links
Private link service allow to expose an Azure workload to consumers with a Private Endpoints just like Azure resources. When creating a service we hare two sides :
- Service producer : responsible to create, manage the workload and expose it using Private Link service
- Service consumer : consuming the service provided using a Private Endpoint
Process
This document will be providing general guidance how to setup such scenario on both sides. Illustration bellow document the example we will be discussing in this document.
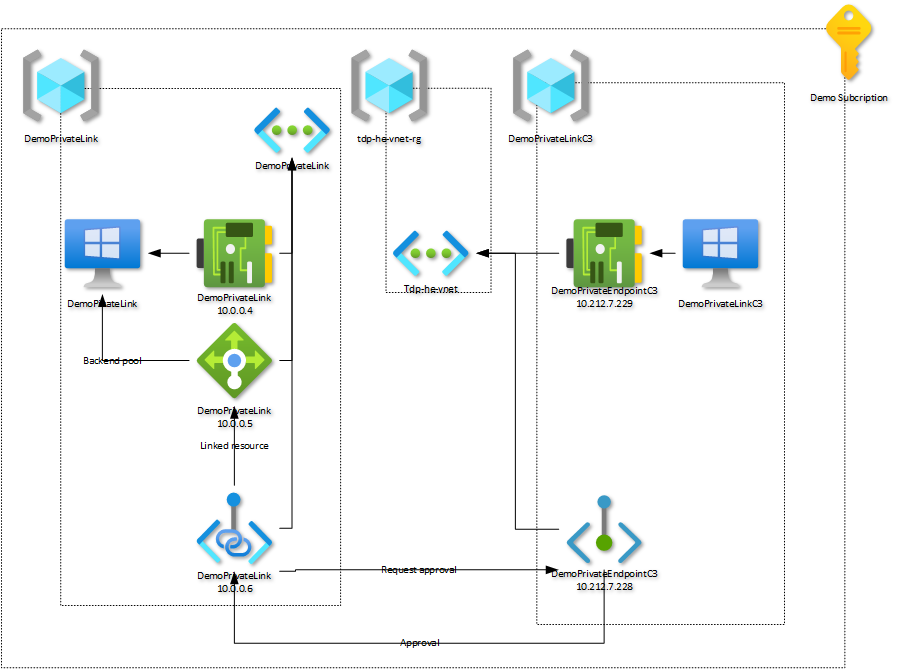
Within a C3 Azure hardened subscription we created a dedicated virtual machine named DemoPrivateLinkC3 that is connected to the tdf-he-vnet. This is the service consumer side. On the left side of the diagram we have the workload hat will be exposed as a service with Private Endpoint.
Service produced
This section document how to expose a workload to be consumed from another Virtual Network in the same Azure Hardened subscription. at TDF, we do not apply any restriction on this side. TDF BL consumers are responsible of their workloads.
Setup workload to be exposed
Setup phase include the following steps :
- Create a dedicated Virtual Network
- Deploy your workload
- Expose your workload
- Create the Private Link
Create a dedicated Virtual Network
Workload to be exposed by a Private Link must located on a dedicated Virtual Network in your C3 Azure Hardened subscription. In diagram, the DemoPrivateLink Virtual Network is not configured for Peering. Virtual Network must remain Isolated. Access to workload will rely on a Private Endpoint linked to a Private Link. FOr this reason, Address space to be used for DemoPrivateLink does not have to be compatible with TDF or Thales IP ranges.
Deploy your workload
Workload created for this documentation is a simple virtual machine with a web server. This virtual machine must be connected to the DemoPrivateLink Virtual Network.
Expose your workload
In order to expose the workload using Private Link, we must deploy an Azure Load Balancer and link it to our workload. Load Balancer must be configured as documented bellow :
- Azure Load Balancer must be in the same C3 Landing zone as the workload to be exposed
- Azure Load Balancer must be provisioned using the Standard SKU (not Basic)
- Azure Load Balancer must be provisioned in internal Load Balancer (No direct public exposition allowed in a C3 Azure hardened subscription)
- Azure Load Balancer must be connected to the same Virtual Network as the workload to be exposed
Virtual machine / Virtual machines ScaleSet workloads must be configured as member of the backend Pool. Configuration of the load balancer must include :
- A frontend IP configuration using a Private IP from
DemoPrivateLinkVirtual Network. - A backend pool with members
- A Health probe to validate backend pool health
- A Load Balancing rule including the front end IP, backend pool and Health Probe
Create the Private Link
Workload to be exposed must be presented using an Private Link Service configured as documented bellow:
- Private Link service must be in the same C3 Landing zone as the workload to be exposed
- Private Link service must be in the same Azure region as the Standard Load Balancer previously created
- Private Link service must be connected to the
DemoPrivateLinkVirtual Network. - Private Link must be configured with Access security restricted by Azure Subscription and limited to the current subscription only as illustrated bellow
- Private Link access security to selected Azure subscription should be configured for
Auto-Approveonly for your subscription
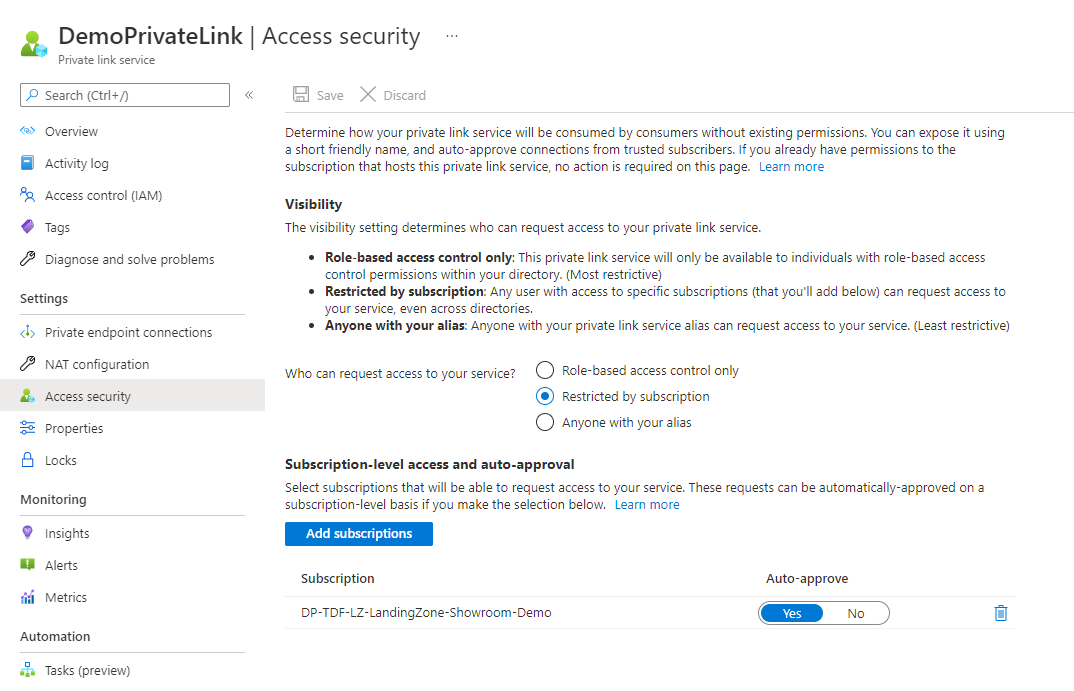
Configuration Anyone with your alias is strictly forbidden as any Azure consumer having your Private Link service resource ID would be able to establish a link with your workload.
service consumer
From a consumer point of view we need to establish a link with the exposed workload by creating a Private Endpoint linked to the private link. This Private Endpoint must be configured as documented bellow:
- Private Endpoint Connection method must be configured to Connect to an Azure resource in my Directory
- Private Endpoint Connection resource type must be configured to Microsoft.Network/PrivateLinkServices
- Private Endpoint resource must be located in the same Azure region
- Private Endpoint resource must be linked to the
tdf-he-vnetVirtual Network - Private Endpoint must be connect to a subnet on witch the private endpoint Policies have been disabled (See prerequisites)
Private Endpoint may need approval from the service producer side.