Configure Private Bastion
This document aims to provide required information to understand the networking services provided by TDF to your Azure Hardened environments. Required vocabulary is available in the Glossary.
Introduction
C3 Azure hardened Subscriptions have a bastion service to access the subscription VM from the TDF network. The Bastion service is required to introduce a protocol break (RDP & SSH) to reach virtual machines connected to TDF managed virtual networks in the Azure Hardened environment.
Because Azure DevTest service is not compliant with C3 security guidelines, service will be replaced in a near future.
The private Bastion service is reachable from TDF BL clients using the ZPA service. It is also available from a web browser through the Azure portal.
In order to provide a more configurable service to TDF consumers, Private Bastion service provide not using virtual machines but Azure DevTest Labs. This service offer to TDF consumer multiple option to customize the service they need:
- Select a set of OS images and virtual machines SKU
- Ability to share a virtual machine between consumers
- Ability to customize provisioned virtual machines with chocolatey
- Ability to rebuild virtual machines
- Set lab policies to automatically shut down and start up virtual machines
- Set caps on your lab, such as the number of virtual machines per user and per lab
- Use the lab cost trend to estimate your spending and set a threshold
- Use custom images to quickly reproduce your environment
- Create formulas to easily modify an environment's configuration at any time
- Enforce expiration date for virtual machines provisioned with DevTest Labs
Architecture
Diagram bellow document Private bastion architecture in an Azure Managed Environment
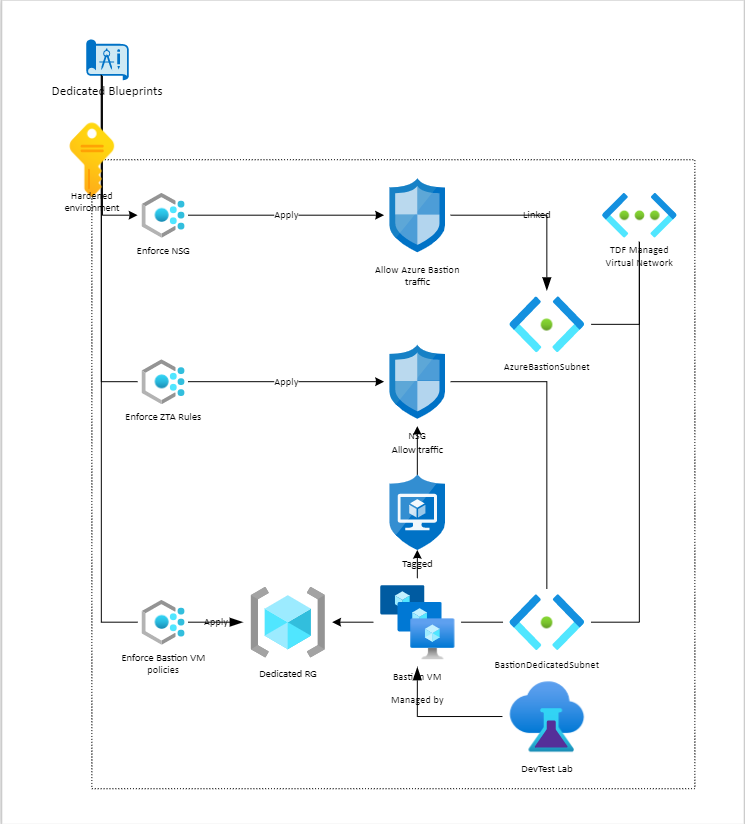
DevTestLab configuration includes:
- Virtual machines created with DevTest Labs will be connected to the bastion dedicated subnet (private-bastion) in the TDF Managed Virtual Network (
tdp-he-vnet) - Virtual machines created with DevTest Labs will be created in a dedicated resource group (
Tdp-he-private-bastion-vm-rg)
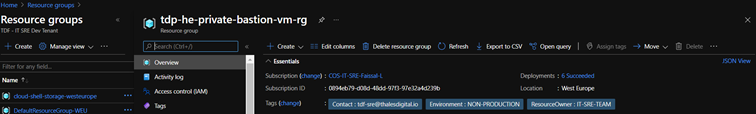
Related services
Dedicated subnet
A dedicated pre-provisioned subnet is provisioned in the TDF managed virtual network for DevTests Labs related virtual machines. This subnet is required to apply a network security group that implements the inbound network flow restrictions required for ZPA access.
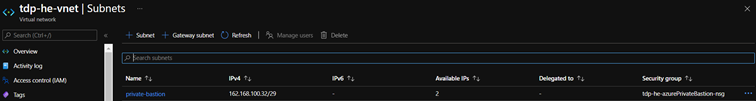
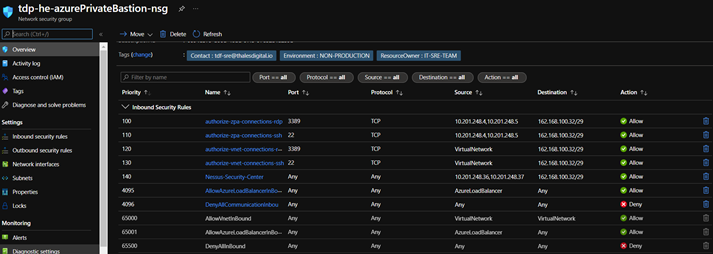
ZPA Access
Only Private Bastion related virtual machines are reachable from the ZPA service. This is a security requirement of the TDF. As consequence:
- Each virtual machine provisioned for DevTest Labs must be located on a dedicated Subnet of the TDF Managed Virtual Network (required to enforce NSG)
- Network flow that reach virtual machines provisioned for DevTestLabs must be hardened:
-
- Source traffic must be limited to ZPA private IP*
-
- No Public Internet Access allowed*
-
- Protocols exposition must be limited to RDP & SSH and required tools from the SOC teams (Nessus, ...)*
How to
Configuration private bastion (Windows)
- Sign in to the azure portal.
- From the main menu on the left side, select Resource groups
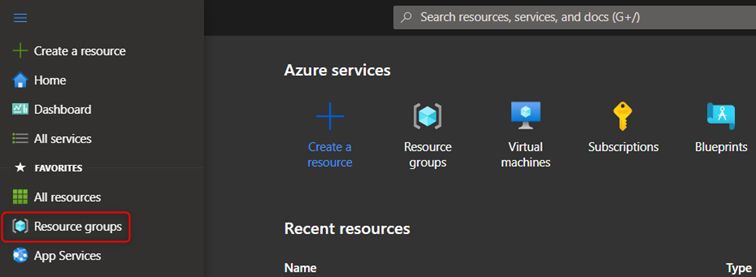
- Select
tdp-heprivate-bastion-rg
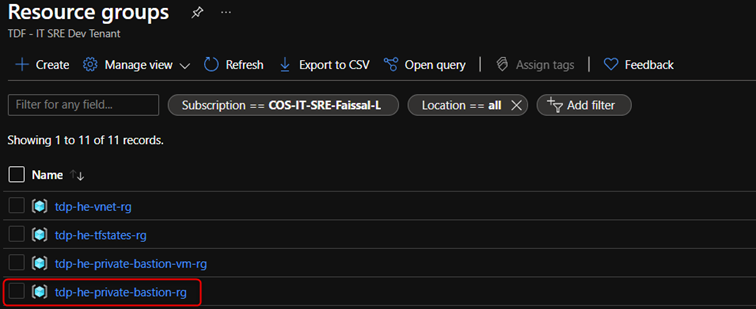
- From the list, select the lab (
PrivateBastionTdp) where the Private bastion will be created
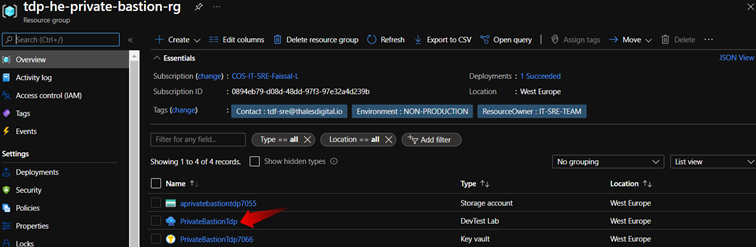
- On the lab's Overview page, select + Add.
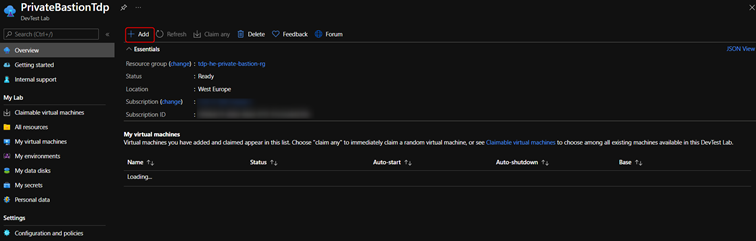
- On the Choose a base page, select a marketplace image for the VM (Windows).
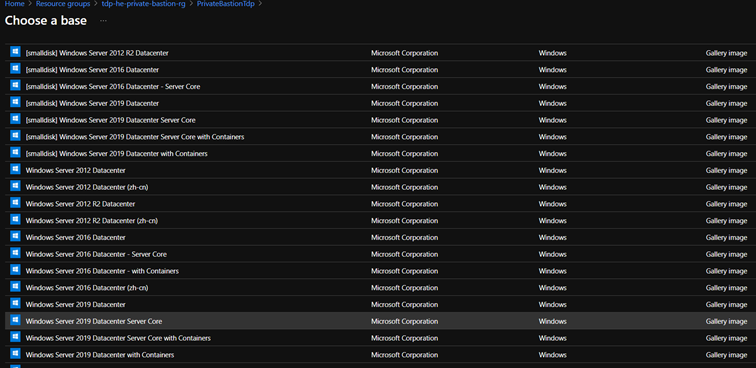
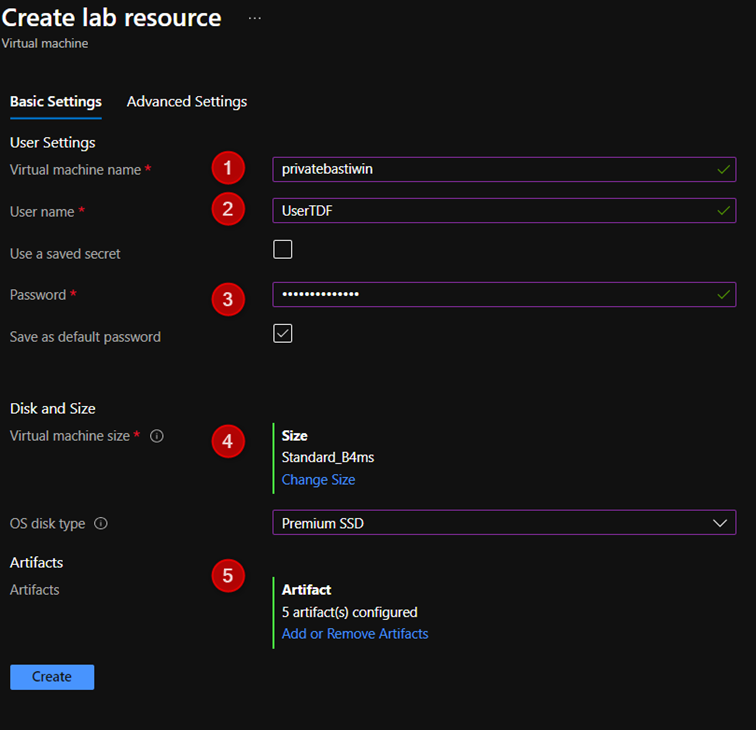
- On the Basic Settings tab of the Virtual machine page, do the following actions:
- Enter a name for the VM in the Virtual machine name text box.
- Enter a Username that is granted administrator privileges on the virtual machine.
- Enter a password for the user.
- select Change size. Select one of the predefined items that specify the processor cores, RAM size, and the hard drive size of the VM to create.
- Select Add or Remove Artifacts. Select and configure the artifacts that you want to add to the base
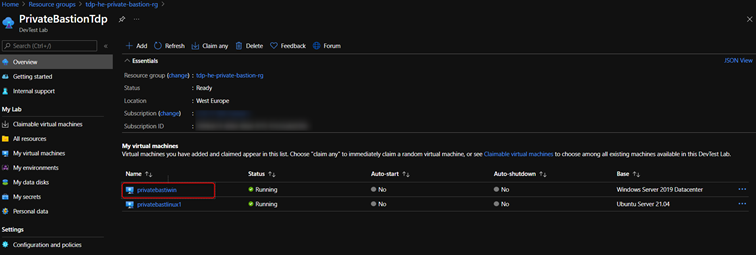
- Select Create to add the specified VM to the lab. The lab page displays the status of the VM's creation - first as Creating, then as Running after the VM has been started.
Configuration private bastion (Linux)
Repeat steps 1 to 5 of the Configuration private bastion (Linux) section.
- On the Choose a base page, select a marketplace image for the VM (Linux).
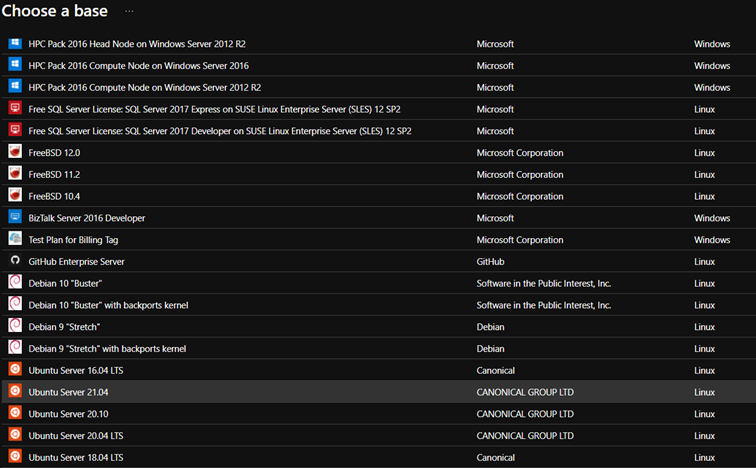
- On the Basic Settings tab of the Virtual machine page, do the following actions:
- Enter a name for the VM in the Virtual machine name text box.
- Enter a Username that is granted administrator privileges on the virtual machine.
- Select password or SSH public key
- Enter a password
- select Change size. Select one of the predefined items that specify the processor cores, RAM size, and the hard drive size of the VM to create.
- Select Add or Remove Artifacts. Select and configure the artifacts that you want to add to the base image.
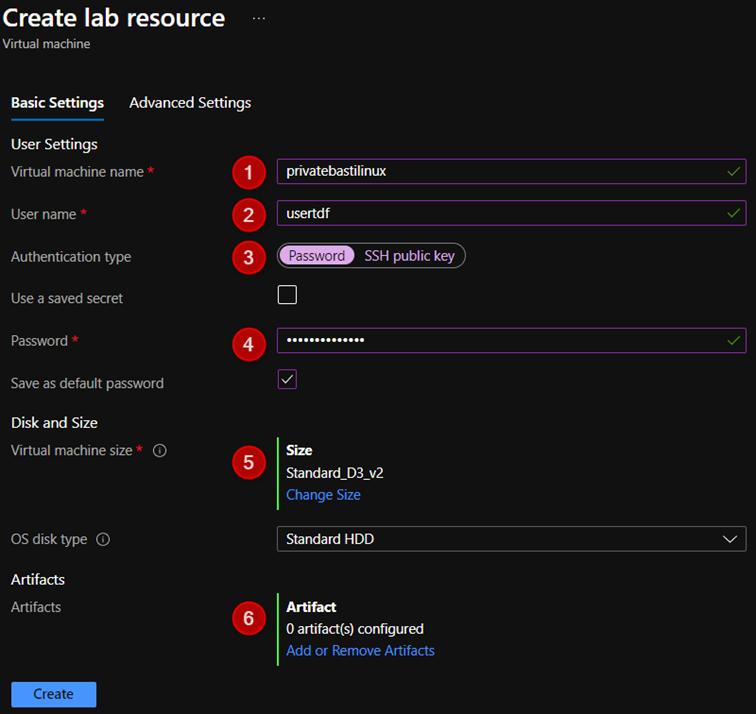
- Select Create to add the specified VM to the lab. The lab page displays the status of the VM's creation - first as Creating, then as Running after the VM has been started.
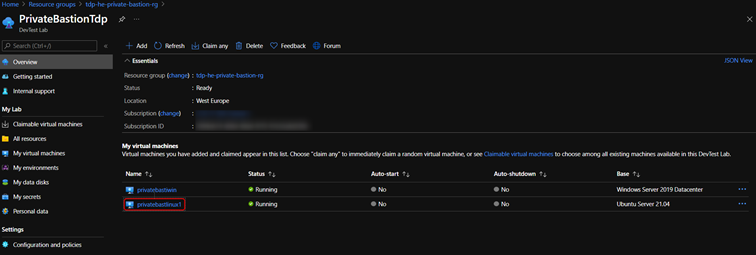
Connect to a private bastion
We have set up a configuration to connect to your private bastion in two ways. RDP/SSH or a web browser (with azure bastion).
To connect via RDP or SSH you must first be connected to the z-scaler VPN, otherwise you will not be able to connect to your server.
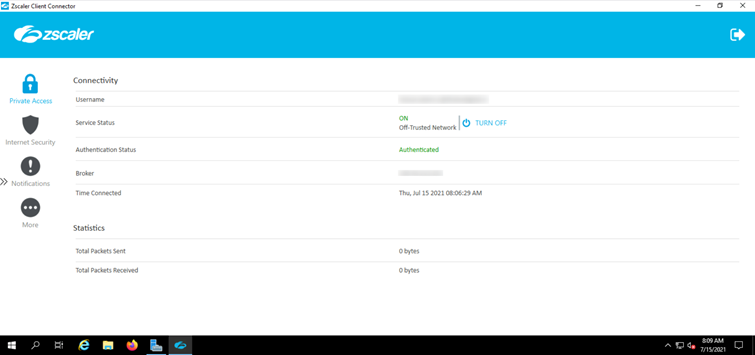
Link to install z-scaler : https://dwp.thalesdigital.io/docs/DOC-3046
Important point when the virtual machine will be created it will be necessary to contact the support team (support@thalesdigital.io) with the IP and port of your machine so that it configures the private access via Z-Scaler for your profile. Link with more information: https://gitlab.thalesdigital.io/just-do-it/it-sre/hardened-landing-zone-documentation/-/blob/master/security/accessing-the-landing-zone.md
Connection RDP
- On the home page for your lab, select your Windows VM from the My virtual machines list.
- On the Virtual machine page for your VM, select Connect on the toolbar
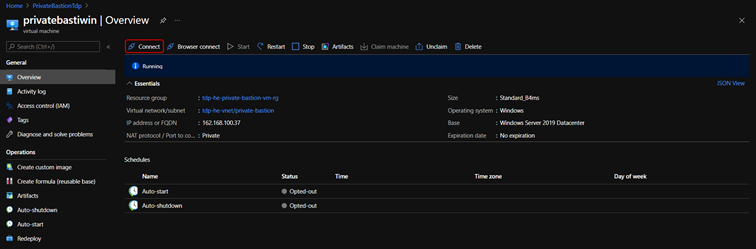
- Open the RDP file and enter your VM credentials that you typed when creating the VM. You should be connected to the Windows VM now.
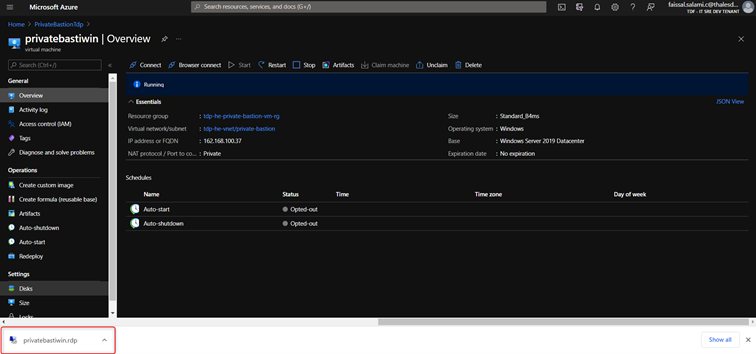
- Open the RDP file.
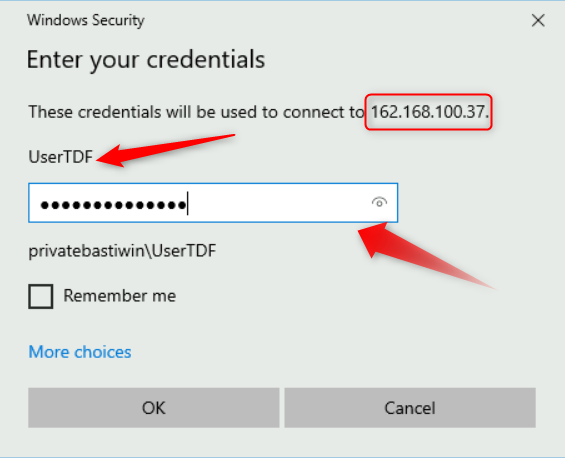
- Enter your VM credentials that you typed when creating the VM.
- You should be connected to the Windows VM now.
Connection SSH
- On the home page for your lab, select your Linux VM from the My virtual machines list.
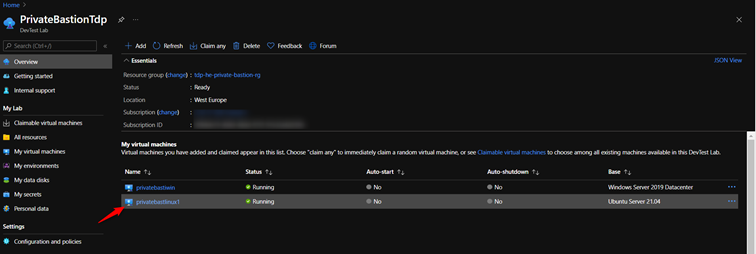
- On the Overview page, you can see the fully qualified domain name (FQDN) or IP address of the VM.
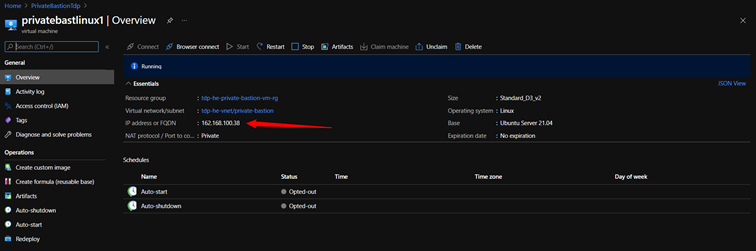
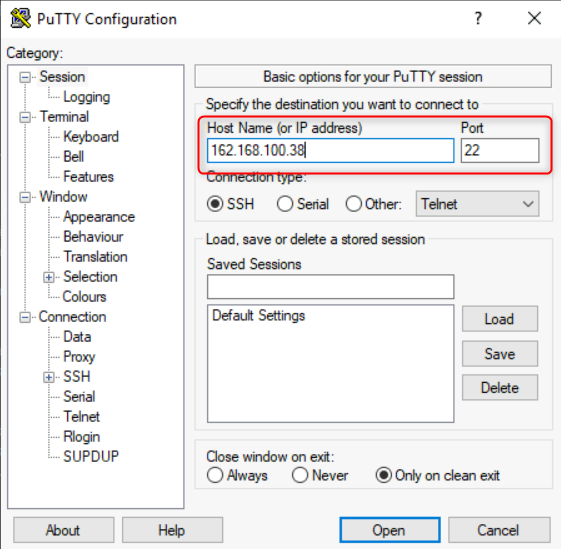
- Enter your connection settings:
- Host Name: FQDN or IP
- Port: 22 (leave as default)
- Connection Type: SSH (leave as default)
- Once the SSH Connection is open, you should see a terminal prompt asking for your username:

- Next, enter your password.
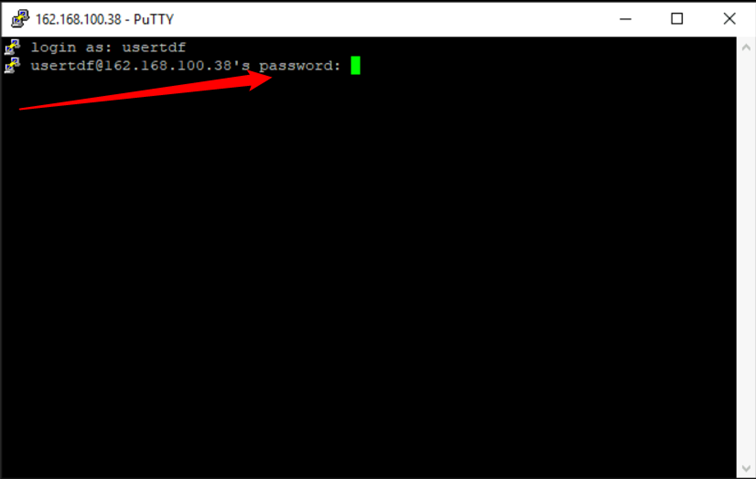
- You are now logged into your server with SSH.
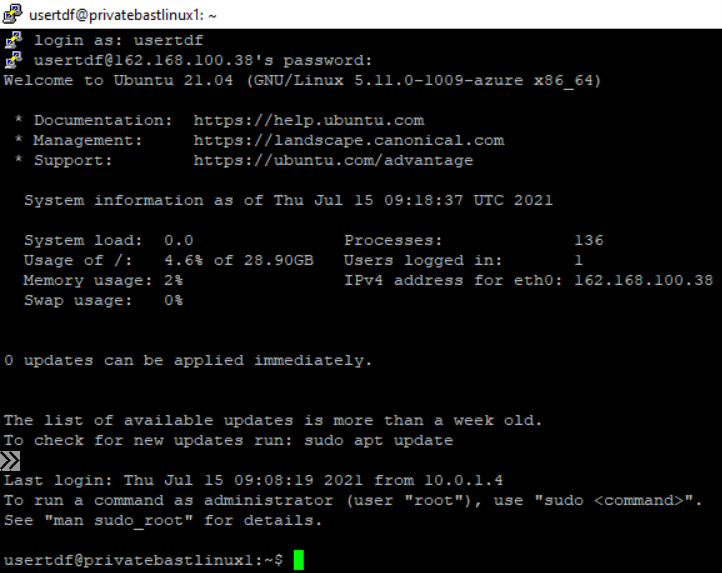
Connection with a browser
To connect with the browser you do not need to be connected to the VPN
- On the home page for your lab, select your Linux/Windows VM from the My virtual machines list.
- On the Virtual machine page for your VM, select Browser Connect on the toolbar.
windows
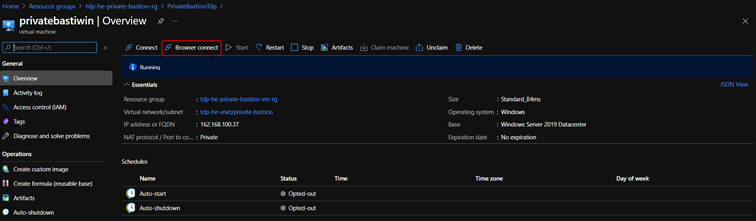
Linux
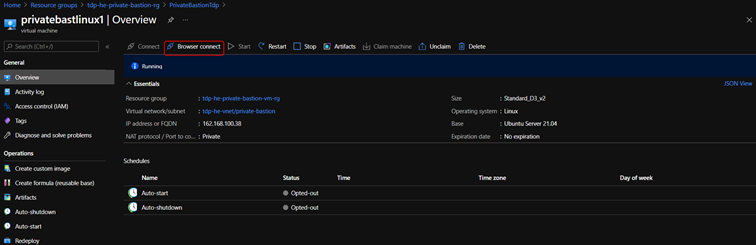
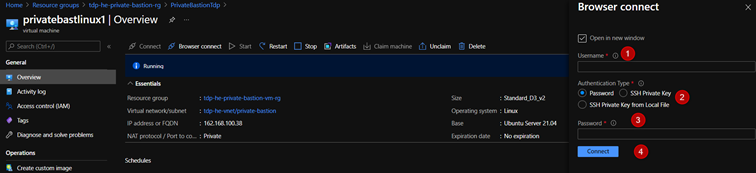
- On the Browser connect page for your VM enter your VM credentials. Select Connect.
windows
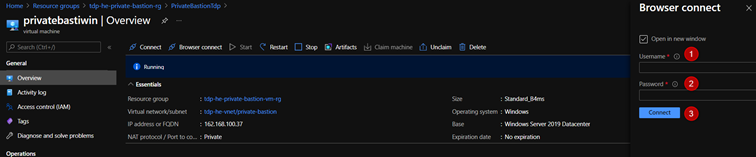
Linux
- The RDP connection to this virtual machine via Bastion will open directly in the Azure portal using port 443 and the Bastion service.
windows
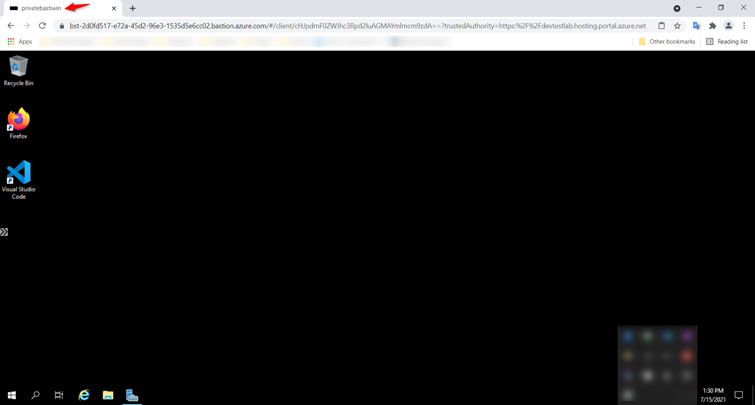
Linux
Other solution
DevTest Lab does not match the need.
You can create a jump box virtual machine which must be linked to the following subnet: tdp-he-azurePrivateBastion-nsg